IaC tools have become essential for managing cloud infrastructure at scale, with the market reaching $1.4 billion in 2025 and growing at 24% annually. When misconfigurations cause outages or manual provisioning creates bottlenecks, organizations face reliability issues and collaboration challenges. Security concerns add urgency to these operational problems—73% of enterprises experienced AI-related security incidents last year, with each breach averaging $4.8 million in costs.
Infrastructure as code addresses these challenges by enabling teams to define entire environments through version-controlled, testable configurations rather than manual console operations. This approach replaces error-prone clicking through interfaces with programmatic infrastructure definitions that can be reviewed, tested, and deployed systematically. The shift gains momentum as AI generates 25% of new code according to Google, yet typical workflows remain problematic: someone writes Terraform, submits a pull request, and relies on colleagues to catch security issues like inadvertently opened ports.
Testing dozens of infrastructure as code platforms across production environments over two decades has shown me which tools deliver reliable automation and which create new operational burdens. This guide examines 16 IaC solutions for 2026, focusing on practical capabilities that matter for teams managing real infrastructure. Organizations can apply the same development rigor—code reviews, testing, security scanning—to infrastructure that governs application development. The analysis covers flexible platforms like env zero that support multiple IaC frameworks with unlimited concurrency, alongside specialized tools designed for specific cloud environments, helping you match capabilities to your automation requirements.
env zero
env zero operates as an infrastructure automation platform that enables self-service infrastructure with guardrails, addressing the operational challenges teams face when managing cloud environments across multiple frameworks. The platform distinguishes itself by supporting diverse IaC tools while maintaining governance controls that prevent the security and cost issues common in manual infrastructure management.
env zero Key Features
The platform delivers multi-framework automation supporting Terraform, OpenTofu, Pulumi, CloudFormation, and Kubernetes, eliminating the need for teams to standardize on a single IaC tool. This flexibility proves essential for organizations with diverse technical teams or legacy infrastructure components.
env zero's drift detection capabilities automatically identify discrepancies between declared infrastructure state and actual cloud resources, providing remediation options that prevent the compliance violations and cost overruns discussed earlier. Custom workflows orchestrate complex deployments across multiple stacks and dependencies, enabling teams to manage intricate infrastructure relationships systematically.
The platform's Cloud Compass feature uses AI-assisted analysis to identify IaC coverage gaps, helping teams understand which cloud resources remain outside their infrastructure as code management. This capability addresses a common blind spot where manual resources create security and compliance risks.
env zero Pros and Cons
Pros:
- Unlimited concurrent deployments with no extra fees
- Multi-framework support across all major IaC tools
- Comprehensive cost controls including estimation, monitoring, and budget alerts
- Self-service capabilities with governance guardrails
- AI-powered insights through Cloud Analyst
- Ready-to-use Policies and Code Optimizer make it easy to implement policy as code and IaC security scanning
Cons:
- Learning curve for teams new to IaC automation
- Some advanced features only available in higher pricing tiers
- Requires integration setup for maximum value
env zero Pricing
env zero employs environment-based and per-apply pricing rather than resource-based billing, providing cost predictability that resource-based models often lack. The platform offers both SaaS and self-hosted deployment options to accommodate different organizational requirements. Pricing typically starts with a base package containing core automation features, with Navigator and Pilot tiers adding advanced capabilities.
env zero Best Use Cases
Organizations with complex, multi-cloud infrastructure benefit most from env zero's comprehensive approach to IaC automation. The platform's self-service capabilities prove particularly valuable for teams where infrastructure expertise varies across members. DevOps organizations experiencing deployment bottlenecks find env zero's automation enables developers to provision resources independently while maintaining governance controls.
Cost-conscious organizations report significant savings through env zero's comprehensive cost management features, with some achieving up to 45% reductions in cloud expenses. The platform serves enterprises requiring strong governance frameworks alongside teams seeking to accelerate developer productivity without compromising security or operational reliability.
Get started by requesting a demo of env zero today to see how its flexible platform can transform your infrastructure automation while maintaining essential controls.
Terraform

Image Source: Medium
Hashicorp Terraform has established itself as the leading Infrastructure as Code tool with 32.8% market share, functioning as a platform-agnostic framework that enables teams to define and provision cloud infrastructure through declarative configuration files. This widespread adoption reflects Terraform's ability to address the complexity of managing resources across multiple cloud providers through a unified approach.
What Are Terraform's Core Capabilities?
Terraform's primary strength lies in its multi-cloud workflow that provides consistent operations across different providers. The tool employs HashiCorp Configuration Language (HCL), a declarative syntax designed specifically for describing desired infrastructure states rather than implementation steps. Terraform's built-in state management creates a mapping between configuration and deployed resources, enabling drift detection and change planning before execution.
The platform's architecture delivers several operational advantages:
- Agentless design eliminating software installation requirements on managed infrastructure
- Module system enabling code reusability and adherence to DRY principles
- Extensive provider ecosystem supporting thousands of services across cloud platforms
- Version-controlled configurations facilitating team collaboration and change tracking
What Are the Trade-offs When Using Terraform?
Strengths:
- Multi-cloud support providing consistent syntax across different providers
- Declarative approach focusing on desired end state rather than procedural steps
- Modular design promoting standardization and infrastructure reuse
- Strong community ecosystem with comprehensive documentation and examples
- Native CI/CD integration supporting tools like GitHub Actions and GitLab
Limitations:
- 2023 license change from Mozilla Public License to Business Source License
- Learning curve for teams transitioning to Infrastructure as Code approaches
- State file management complexities in collaborative team environments
- Potential delays in supporting newly released cloud provider features
How Does Terraform Pricing Work?
The core Terraform CLI remains available at no cost. HCP Terraform (formerly Terraform Cloud) provides enhanced collaboration features through tiered pricing:
- Free tier: Supports up to 500 managed resources
- Essentials: $0.10 per managed resource monthly beyond the 500-resource threshold
- Standard: $0.47 per managed resource monthly with advanced workflow features
When Should Organizations Choose Terraform?
Terraform excels for organizations requiring consistent infrastructure management across multiple cloud platforms. The tool proves particularly effective for multi-tier applications where resource dependencies must be managed systematically. Teams with established DevOps practices find Terraform valuable for standardizing infrastructure deployment workflows. Organizations seeking greater operational flexibility with unlimited concurrency across all IaC frameworks might consider env zero as a more comprehensive platform alternative.
OpenTofu

Image Source: The New Stack
OpenTofu emerged as a community-driven fork of Terraform following HashiCorp's license change from the open-source Mozilla Public License to the more restrictive Business Source License in 2023. Subsequently placed under Linux Foundation stewardship, this tool ensures infrastructure as code remains truly open source. The fork addresses concerns about vendor control while maintaining compatibility with existing Terraform workflows.
How Does OpenTofu Extend Terraform's Capabilities?
OpenTofu maintains complete compatibility with existing Terraform configurations while expanding capabilities through community-driven development. The platform introduces several distinctive enhancements that address common operational challenges:
State encryption provides built-in protection for sensitive infrastructure data with multiple key providers including PBKDF2, AWS KMS, and GCP KMS. This addresses compliance requirements that previously required external tooling or complex workarounds.
Dynamic provider configurations enable configuration generation using for_each loops, particularly valuable for multi-region or multi-account scenarios where static configuration becomes unwieldy. Resource exclusion allows selective exclusion of resources from operations with the -exclude flag, improving operational flexibility during maintenance or troubleshooting. Early variable evaluation permits using variables and locals in terraform blocks and module sources, reducing configuration complexity.
What Are OpenTofu's Current Strengths and Limitations?
OpenTofu's primary advantage lies in its truly open-source nature with Mozilla Public License 2.0 guaranteeing unrestricted use. Community-driven development ensures continued innovation without vendor gatekeeping, while vendor-neutral governance through Linux Foundation provides long-term stability. The tool functions as a drop-in replacement for Terraform, preserving existing workflows and minimizing migration overhead.
However, OpenTofu faces challenges typical of newer projects. The relatively recent fork means a smaller ecosystem of integrations and support options compared to established alternatives. Potential compatibility challenges with newer Terraform features may emerge as the projects diverge. Teams evaluating OpenTofu must weigh these current limitations against the long-term benefits of vendor independence.
OpenTofu Pricing and Economic Considerations
OpenTofu remains completely free and open-source with no commercial restrictions. This contrasts sharply with Terraform's tiered pricing model, making OpenTofu particularly cost-effective for startups and large enterprises facing resource-based billing concerns. The absence of licensing fees can represent significant savings for organizations managing extensive infrastructure deployments.
When Should Organizations Consider OpenTofu?
OpenTofu works exceptionally well for organizations prioritizing vendor neutrality and open-source governance. Companies requiring built-in state encryption for compliance or security requirements find OpenTofu's native capabilities particularly valuable. The tool suits teams comfortable with community-supported software and those seeking to avoid potential future licensing restrictions.
Organizations concerned about vendor lock-in or requiring guaranteed access to source code will find OpenTofu's Linux Foundation stewardship compelling. However, teams needing extensive third-party integrations or commercial support may prefer more established alternatives until OpenTofu's ecosystem matures.
Pulumi
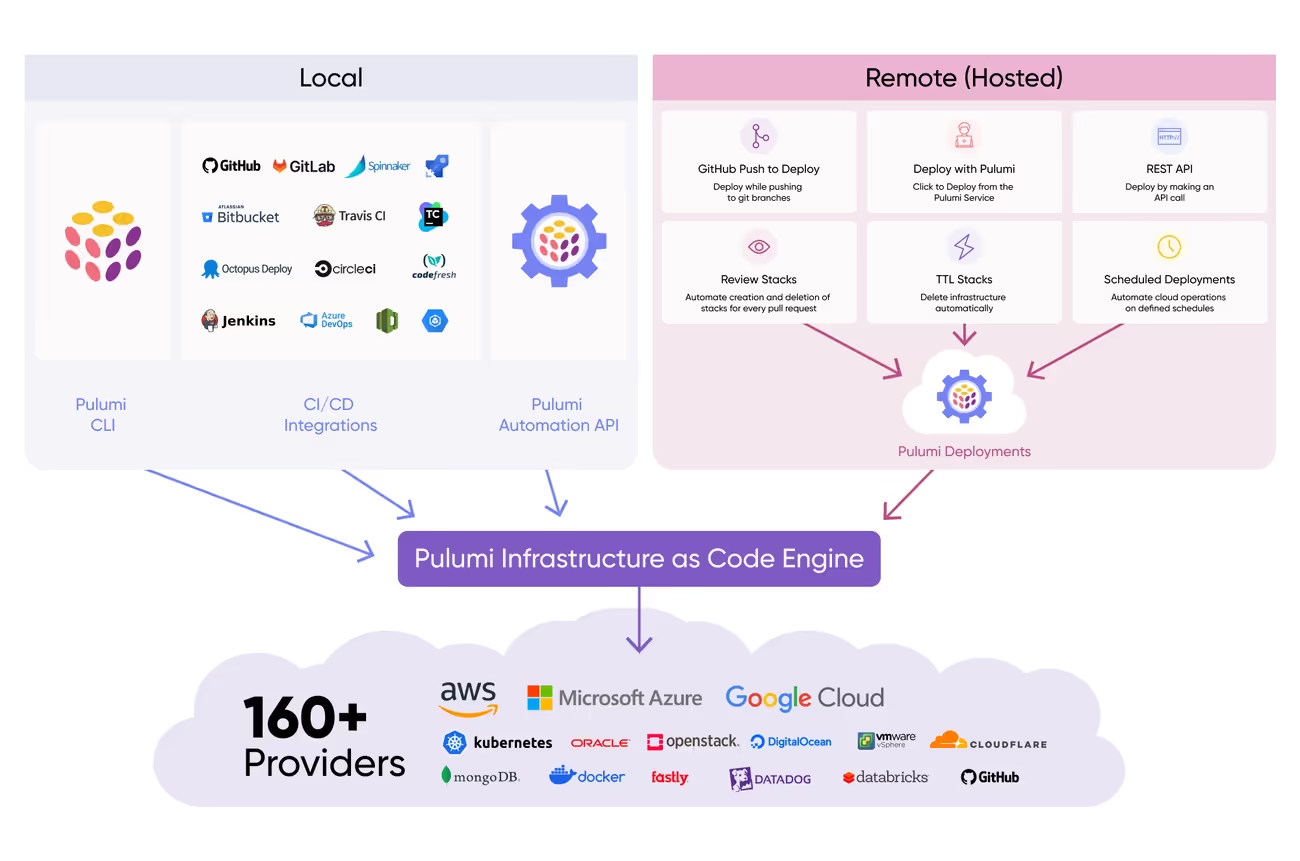
Image Source: Pulumi
Pulumi shifts infrastructure as code from domain-specific languages to general-purpose programming languages, enabling teams to define infrastructure using Python, TypeScript, Go, C#, and Java alongside YAML for simpler configurations. This approach eliminates the need to learn proprietary configuration syntaxes while applying familiar development practices to infrastructure management.
How Does Pulumi Support Multiple Programming Languages?
The platform's multi-language architecture allows teams to choose languages that match their existing expertise rather than learning new DSLs. Pulumi provides same-day access to new cloud features across 150+ providers, ensuring teams can adopt the latest capabilities immediately without waiting for configuration language updates.
Pulumi delivers comprehensive testing frameworks that enable unit, property, and integration tests for infrastructure code. The developer experience includes full IDE support with IntelliSense, debugging, and refactoring capabilities. Built-in secrets management automatically encrypts sensitive information both in transit and at rest, addressing security concerns without additional tooling.
What Are Pulumi's Strengths and Limitations?
Advantages:
- Familiar programming languages reduce learning overhead for development teams
- Rich programming constructs enable loops, conditionals, and functions in infrastructure definitions
- Multi-cloud flexibility through native provider SDKs
- Apache 2.0 open-source licensing ensures long-term availability
- Infrastructure testing capabilities mirror application development practices
Trade-offs:
- Programming background required, creating barriers for operations-focused teams
- Smaller ecosystem compared to established tools like Terraform
- Advanced scenarios may require complex implementation patterns
- Risk of over-engineering infrastructure code without proper discipline
How Does Pulumi Pricing Compare to Alternatives?
Pulumi offers tiered pricing beginning with a free tier for individual developers. The Team tier includes 150,000 monthly credits with standardized billing for additional usage. Enterprise and Business Critical tiers add RBAC, SAML/SSO integration, and compliance tools. Organizations seeking predictable costs might consider env zero as an alternative with unlimited concurrent deployments and environment-based rather than resource-based billing.
When Does Pulumi Deliver the Most Value?
Teams with strong software engineering backgrounds benefit most from Pulumi's approach, particularly when applying mature development practices to infrastructure. The platform excels for dynamic infrastructure scenarios requiring resource creation based on external data or complex business logic. Organizations report significant productivity improvements, with some achieving 80-90% deployment time reductions when transitioning from traditional IaC approaches.
For teams seeking flexibility across all IaC frameworks with unlimited concurrency, env zero provides more comprehensive coverage, especially valuable when not all team members are infrastructure experts.
Spacelift
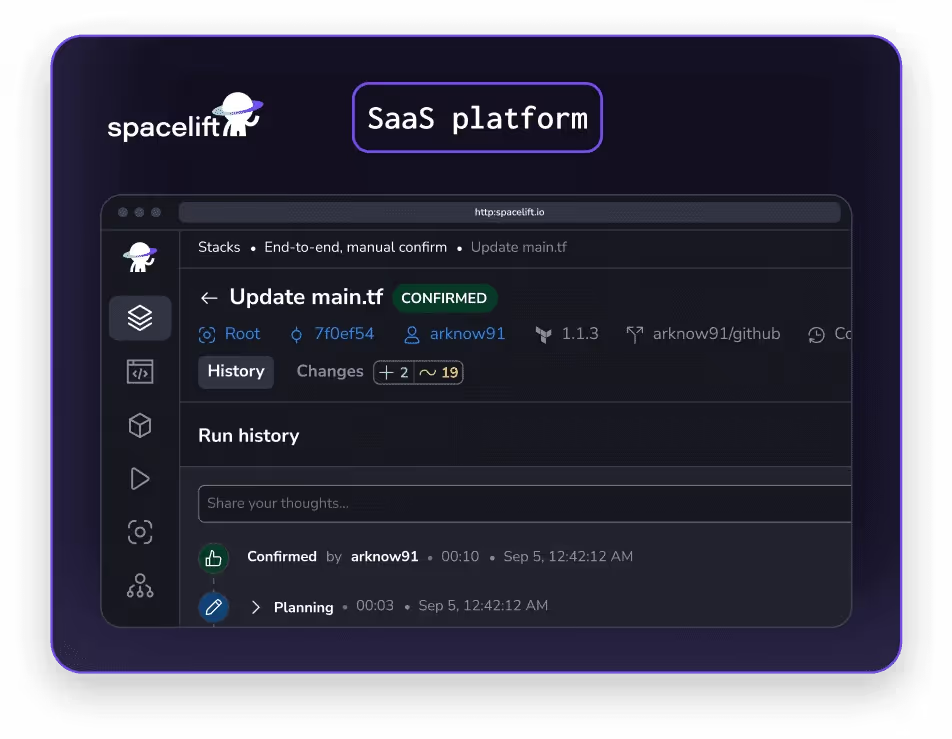
Image Source: Spacelift
Spacelift functions as a multi-tool infrastructure orchestration platform that coordinates Terraform, OpenTofu, Ansible, CloudFormation, and Kubernetes deployments through unified workflows. The platform addresses the operational complexity that emerges when teams manage infrastructure using multiple IaC tools across different environments and compliance requirements.
What Are Spacelift's Core Capabilities?
Spacelift's architecture centers on stack dependencies that enable orchestration of complex multi-layer deployments across different tools. The platform implements Open Policy Agent-based policies for governance at multiple decision points throughout the deployment lifecycle. Drift detection operates continuously to identify unauthorized infrastructure changes, with configurable remediation workflows. Resource visualization provides unified visibility across all deployed infrastructure regardless of the underlying tool.
Additional operational capabilities include private module and provider registries with CI integration, advanced scheduling for runs and drift detection, and GitOps workflows that support diverse Git branching strategies and monorepo structures.
How Does Spacelift Compare to Alternative Platforms?
Strengths:
- Multi-tool coordination capabilities that handle complex operational dependencies
- OPA-based policy enforcement ensuring compliance across different IaC frameworks
- Self-service infrastructure through blueprint automation that standardizes deployment patterns
- Concurrency-based pricing that provides predictable costs regardless of resource count
Limitations:
- Free tier restrictions exclude deployment notifications and advanced workflow features
- Self-hosted deployments provide reduced functionality compared to SaaS offerings
- Version synchronization challenges between different platform releases can affect workflow stability
- Feature complexity may exceed operational requirements for smaller organizations
What Does Spacelift Cost?
Spacelift structures pricing around user count and worker capacity rather than managed resources. The Starter plan costs $399 monthly for 10 users with 2 public workers. Business and Enterprise tiers add unlimited users, private workers, and advanced features including blueprints and comprehensive audit trails. This approach provides more predictable cost forecasting compared to resource-based billing models that scale with infrastructure growth.
When Should Teams Choose Spacelift?
Spacelift delivers value for organizations coordinating infrastructure across multiple automation tools. Teams implementing comprehensive policy frameworks for security and compliance find the platform's OPA integration particularly effective. Organizations creating per-PR environments or requiring detailed audit capabilities benefit from Spacelift's workflow orchestration and reporting features. For teams seeking broader flexibility with unlimited concurrency across all IaC frameworks, env zero provides a more versatile solution that accommodates varying levels of infrastructure expertise across team members.
Crossplane

Image Source: www.crossplane.io
Crossplane represents a different architectural approach to infrastructure management, operating as a Kubernetes-native control plane that manages cloud resources through continuous reconciliation rather than manual deployment cycles. This open-source framework extends Kubernetes controller patterns to infrastructure provisioning across multiple cloud providers, creating a unified control plane for both applications and infrastructure.
What Makes Crossplane Different from Traditional IaC Tools?
Crossplane's defining characteristic is its continuous reconciliation model that automatically detects and corrects configuration drift without requiring manual intervention. This contrasts with tools like Terraform that depend on manual plan-apply cycles for changes. The platform extends Kubernetes' declarative management approach to infrastructure, treating cloud resources as Kubernetes objects that maintain desired state continuously.
Platform teams can create high-level abstractions through Composite Resource Definitions (XRDs) and Compositions, enabling developers to request infrastructure via simplified APIs without understanding underlying cloud provider complexities. The system supports programmatic flexibility through "functions" that accommodate languages like Go and Python for dynamic infrastructure configurations.
Crossplane Strengths and Limitations
Crossplane advantages:
- Continuous state reconciliation eliminates manual drift correction
- Infrastructure state stored within Kubernetes, avoiding separate state file management
- Native integration with existing Kubernetes security features including RBAC
- Enables GitOps workflows through standard Kubernetes patterns
- Community-driven development under CNCF governance
Implementation challenges:
- No preview capabilities before applying infrastructure changes
- Requires existing Kubernetes expertise for effective implementation
- Provider installations may affect API server performance
- Component upgrades can occasionally trigger unintended resource deletion
- Complex YAML configurations increase management overhead
How Much Does Crossplane Cost?
Crossplane operates as free, open-source software under Apache 2.0 licensing. Organizations requiring commercial support can access Upbound's tiered offerings:
- Community: Open-source features with no cost
- Standard: Identity integration and patch release support
- Enterprise: Control plane group management capabilities
- Business Critical: Advanced hosting with premium SLAs
When Should You Choose Crossplane?
Crossplane works best for organizations already operating Kubernetes extensively who want to extend that control plane to infrastructure management. Platform engineering teams building developer self-service capabilities find Crossplane's API-driven approach particularly valuable, allowing infrastructure requests through familiar Kubernetes interfaces. Multi-cloud environments benefit from Crossplane's unified API abstraction across providers.
Understanding that Crossplane requires Kubernetes expertise and lacks preview capabilities helps teams assess whether its continuous reconciliation benefits outweigh implementation complexity. For organizations seeking broader IaC framework support with unlimited concurrency, env zero provides a more accessible alternative that accommodates teams with varying infrastructure expertise levels.
AWS CloudFormation
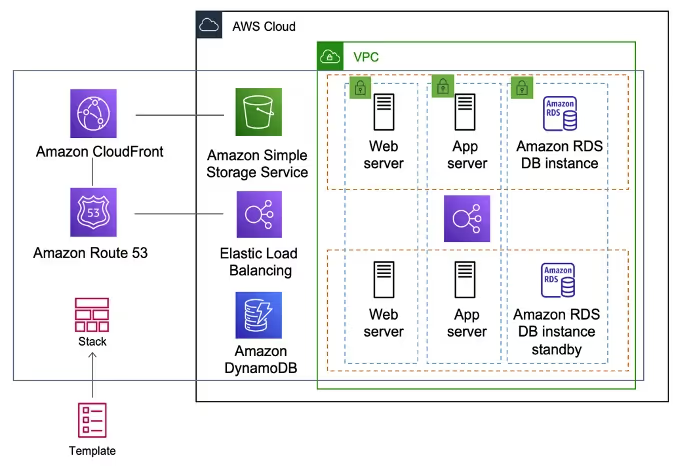
Image Source: AWS Documentation
AWS CloudFormation serves as the native Infrastructure as Code service for Amazon Web Services, enabling teams to model entire AWS environments through template-based architecture using YAML or JSON formats. This declarative service eliminates manual resource configuration while ensuring reproducible deployments across regions and accounts.
AWS CloudFormation Key Features
CloudFormation's template system defines infrastructure through structured YAML or JSON configurations that describe desired resource states. Change sets provide preview capabilities before implementing modifications, allowing teams to identify potential impacts before execution. The service handles resource dependencies automatically, sequencing creation and deletion operations without manual intervention. Drift detection identifies when actual resources diverge from template definitions, supporting compliance and governance requirements.
Key operational features include:
- Automatic rollback when stack operations fail
- Stack policies that prevent accidental resource modification
- Cross-stack references for managing related infrastructure components
- StackSets for deploying templates across multiple accounts and regions
AWS CloudFormation Pros and Cons
Pros:
- Deep integration with all AWS services including same-day support for new features
- Built-in state management eliminating external storage requirements
- No additional service charges beyond provisioned resources
- Native AWS IAM integration for fine-grained access control
Cons:
- AWS ecosystem limitation prevents multi-cloud infrastructure management
- JSON template syntax creates readability challenges for complex infrastructures
- Template modularity requires careful organization to avoid monolithic configurations
- Limited programming constructs compared to general-purpose language tools
AWS CloudFormation Pricing
CloudFormation operations incur no additional charges when using AWS::, Alexa::, or Custom::* resource types. Teams pay only for the AWS resources their templates provision, making cost prediction straightforward for AWS-focused infrastructures.
AWS CloudFormation Best Use Cases
Organizations standardized on AWS find CloudFormation effective for consistent environment provisioning and disaster recovery automation. Teams managing AWS-only infrastructures benefit from its native integration and zero additional costs. CloudFormation works particularly well for compliance-focused environments where template-based governance provides auditable infrastructure definitions.
For organizations requiring broader flexibility across multiple IaC frameworks, env zero offers comprehensive automation that extends beyond single-cloud limitations while maintaining governance controls.
Azure Bicep
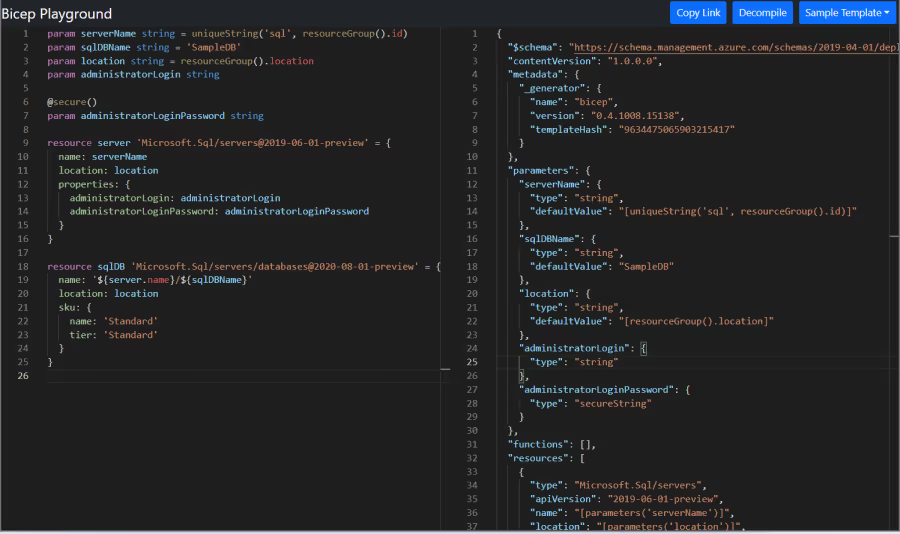
Image Source: Azure Docs
Microsoft's domain-specific language, Azure Bicep, functions as a transparent abstraction over ARM templates, addressing the complexity and verbosity that teams encounter when managing Azure infrastructure through JSON configurations. This Azure-specific tool represents Microsoft's acknowledgment that ARM templates create unnecessary friction for development teams.
Azure Bicep Key Features
Bicep's primary strength lies in its concise syntax that reduces code verbosity by roughly 50% compared to equivalent JSON ARM templates. The language implements modular design patterns that enable developers to create reusable components, promoting standardization across Azure deployments. Understanding resource dependencies becomes simpler because Bicep automatically detects implicit relationships between resources, eliminating manual dependency management. The tool provides day-zero support for all Azure resources and API versions, ensuring immediate access to new Azure capabilities upon release.
Azure Bicep Pros and Cons
Pros:
- Significantly cleaner syntax compared to ARM template JSON
- VS Code extension delivers comprehensive development support including IntelliSense and validation
- Direct Azure Resource Manager integration eliminates separate state management requirements
- Completely free with Apache 2.0 licensing
Cons:
- Azure ecosystem limitation prevents multi-cloud infrastructure patterns
- Limited community resources and examples due to relative newness
- Cannot manage Azure data plane operations, only control plane resources
- Requires learning Microsoft's domain-specific language rather than general-purpose alternatives
Azure Bicep Pricing
Bicep incurs no additional costs beyond the Azure resources provisioned through deployments.
Azure Bicep Best Use Cases
Bicep delivers the most value for organizations standardized on Azure infrastructure who need simpler alternatives to ARM templates. Teams managing complex Azure environments find Bicep's modularity and simplified syntax reduce development time and maintenance overhead. Organizations requiring multi-cloud capabilities or seeking platform-agnostic approaches might evaluate env zero as an alternative that supports multiple IaC frameworks with unlimited concurrency across diverse environments.
Google Cloud Deployment Manager

Image Source: Google Cloud Documentation
Google Cloud Deployment Manager functions as Google's native infrastructure as code service, enabling automated creation and management of GCP resources through declarative templates. Google has announced CDM's deprecation effective December 31, 2025, making this tool's evaluation more about transition planning than long-term adoption.
What Are Google CDM's Key Capabilities?
Google CDM operates primarily through YAML configurations with Python and Jinja2 template support. The platform includes preview mode for reviewing changes before implementation and parallel deployment capabilities where multiple resources deploy simultaneously. CDM automatically handles resource dependencies during deployment, and each project receives unlimited read/delete requests with a daily allowance of 1,000 write requests.
What Are Google CDM's Strengths and Limitations?
Strengths:
- Zero additional costs beyond deployed resources
- Native integration with all Google Cloud services
- Idempotent provisioning ensures consistent results
- Automated rollback during deployment failures
Limitations:
- Restricted to Google Cloud ecosystem exclusively
- Template complexity increases with infrastructure scale
- 1,000 active deployment limit per project
- 1MB configuration file size restriction
How Does Google CDM Handle Pricing?
CDM itself incurs no charges; users pay solely for the Google Cloud resources they provision.
When Does Google CDM Make Sense?
CDM works for organizations fully committed to Google Cloud. However, the upcoming deprecation requires migration planning rather than new implementations. Organizations should evaluate alternatives like env zero, which provides flexibility across all IaC frameworks with unlimited concurrency—particularly valuable for teams where not everyone is an infrastructure expert.
Ansible
Image Source: Red Hat
Red Hat Ansible operates as an automation tool that addresses configuration management and application deployment challenges through agentless architecture and declarative playbooks. This mature solution fills a specific role in the infrastructure automation ecosystem, complementing infrastructure provisioning tools rather than replacing them.
How Does Ansible Address Configuration Management Challenges?
Ansible's agentless design eliminates the operational overhead of installing and maintaining software agents across managed infrastructure. The platform communicates through standard SSH protocols for Linux systems and WinRM for Windows environments. Teams define automation workflows using YAML-based playbooks that describe desired system states without requiring complex programming knowledge. Idempotent execution ensures that running the same playbook multiple times produces consistent results without unintended side effects.
Key automation capabilities include:
- Push-based execution model for immediate task deployment
- Extensive module library covering system administration tasks
- Inventory management for organizing target systems
- Role-based organization for reusable automation components
What Are the Operational Trade-offs of Using Ansible?
Advantages:
- Simple syntax reduces learning curve for operations teams
- No agent infrastructure to secure or maintain on target systems
- Cross-platform support spanning Linux, Windows, and network devices
- Strong community ecosystem with thousands of contributed modules
Limitations:
- GUI capabilities remain limited compared to command-line operations
- Lacks state management for tracking complex resource dependencies
- Windows automation requires Linux-based control nodes
- Better suited for configuration management than infrastructure provisioning
How Does Ansible Pricing Compare to Infrastructure Platforms?
Red Hat Ansible Automation Platform uses node-based pricing tiers:
- Standard edition: $13,000 annually for 100 managed nodes
- Premium edition: $17,500 annually with enhanced support
- Academic pricing available for educational institutions
When Does Ansible Work Best in Infrastructure Workflows?
Ansible excels in scenarios where infrastructure already exists and requires consistent configuration or application deployment. Organizations with established DevOps practices use Ansible to standardize operational procedures across diverse environments. The tool operates effectively in hybrid scenarios where teams need to manage both legacy systems and cloud infrastructure through unified playbooks.
Configuration management represents one component of infrastructure automation, and Ansible addresses this need effectively within its domain. Teams requiring comprehensive infrastructure lifecycle management across multiple frameworks benefit from platforms like env zero that coordinate provisioning, configuration, and governance through unified workflows.
Chef
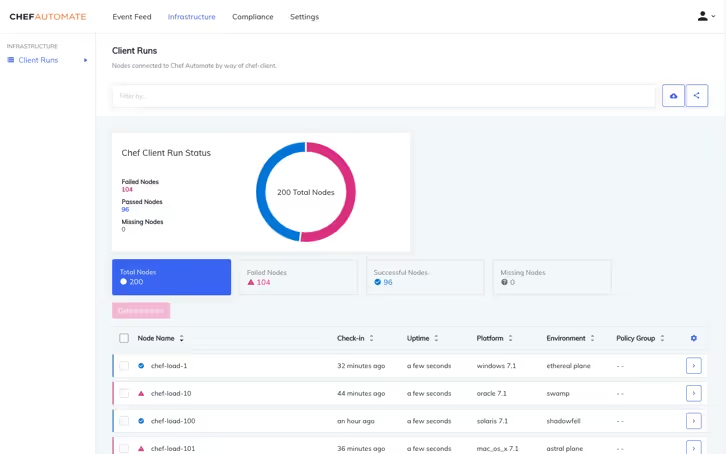
Image Source: Chef
Originally developed by Opscode, Chef operates as an IT automation platform built on Ruby DSL that transforms infrastructure into code through cookbooks and recipes, establishing its position among established IaC tools.
Chef Key Features
Chef's infrastructure automation centers on its Ruby-based DSL that defines reusable recipes. The platform demonstrates particular strength in server management, enabling teams to handle large infrastructures with minimal operations staff. Chef's blueprint maintenance capabilities ensure control and consistency across deployments. The platform also provides seamless integration with popular cloud providers through its hybrid environment capabilities.
Chef Pros and Cons
Pros:
- Manages large, complex infrastructures efficiently
- Improves debugging by monitoring before errors occur
- Streamlines DevOps workflows from building to troubleshooting
- Handles both on-premise and cloud platforms
Cons:
- Steep learning curve, particularly for teams unfamiliar with Ruby
- Pull configuration model can delay immediate actions
- More resource-intensive compared to alternatives
- Cookbook management requires careful coordination
Chef Pricing
Chef's tiered pricing begins with the Business plan at USD 59.00 per node per year. The Enterprise tier costs USD 189.00 per node per year with additional features. Enterprise Plus provides customized pricing with premium support.
Chef Best Use Cases
Chef works particularly well for organizations deploying software rapidly across complex environments. The platform's Ruby requirement makes it most suitable for teams with programming backgrounds. While Chef handles large infrastructures effectively, teams requiring flexibility across all IaC frameworks with unlimited concurrency may find env zero a more versatile solution.
Puppet
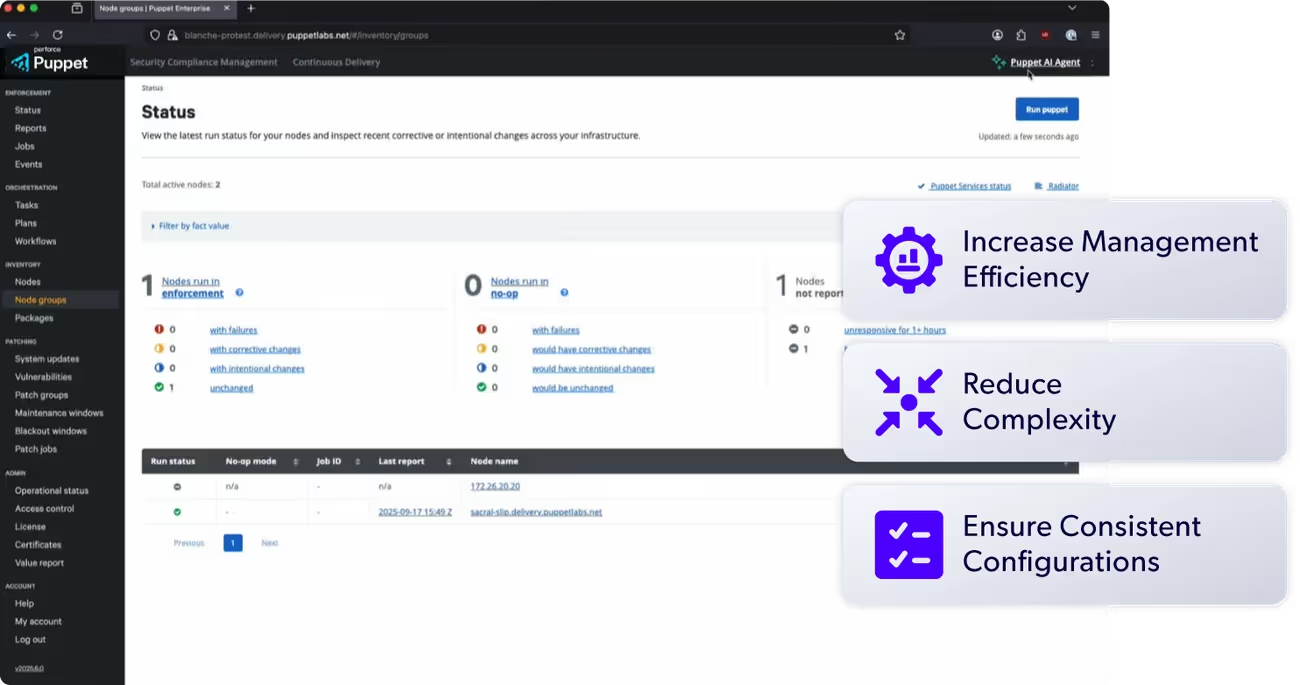
Image Source: Puppet
Puppet functions as an established configuration management platform that automates system administration through declarative state definitions. Released in 2005, this tool represents one of the most mature solutions in the infrastructure automation space, with nearly two decades of production deployments informing its development.
How Does Puppet Handle Infrastructure Automation?
Puppet uses a declarative language similar to XML that focuses on describing desired system states rather than implementation steps. The platform's idempotency ensures changes apply only when necessary, preventing redundant operations that could destabilize systems. Cross-platform support spans Linux, Windows, macOS, and cloud environments, while the centralized management architecture enables control of thousands of servers from a single controller.
The tool operates through a pull-based model where agents periodically check with the Puppet master for configuration updates, creating a different operational pattern compared to push-based tools. This approach provides consistency across distributed environments but introduces timing considerations for immediate configuration changes.
What Are Puppet's Operational Trade-offs?
Puppet delivers consistent configuration management across diverse environments with strong automation capabilities that reduce manual errors. The active community provides extensive modules, and robust reporting capabilities offer visibility into system states and changes. However, extending functionality requires Ruby knowledge, creating a steeper learning curve for teams without programming backgrounds. The agent architecture consumes resources on managed nodes, and performance can degrade with large-scale infrastructure.
How Does Puppet Pricing Compare to Alternatives?
Puppet's tiered pricing ranges from USD 11,200 to 19,900 annually for up to 100 nodes. Open Source Puppet remains available without cost, while Puppet Enterprise adds advanced features including GUI, RBAC, and enhanced reporting capabilities. This pricing structure reflects the platform's enterprise focus but may exceed budget constraints for smaller organizations.
When Should Organizations Choose Puppet?
Puppet excels in regulated industries requiring compliance enforcement and audit trails. Organizations managing large-scale, heterogeneous environments benefit from its mature ecosystem and centralized control capabilities. The platform works particularly well for teams already committed to configuration management workflows and those requiring detailed reporting for compliance purposes.
Teams seeking broader flexibility across infrastructure provisioning and multiple IaC frameworks might consider env zero, which supports comprehensive automation with unlimited concurrency while addressing configuration management alongside infrastructure deployment.
SaltStack
SaltStack, developed by Thomas S. Hatch in 2011, operates as a high-speed infrastructure automation platform built on Python. Originally created after Hatch became frustrated with slower Ruby-based configuration management systems, this tool employs a distinctive master-minion model for remote execution and configuration management.
SaltStack Key Features
SaltStack's event-driven architecture enables real-time remote execution across thousands of machines simultaneously. The platform utilizes ZeroMQ messaging creating an asynchronous network topology that delivers exceptional communication speed. Its state system defines desired configurations through YAML files, ensuring consistent deployments. SaltStack's Pillar feature securely stores and distributes sensitive data like credentials and passwords to minions as needed.
SaltStack Pros and Cons
Pros:
- Exceptional scalability handling thousands of nodes with minimal latency
- Near-instantaneous command execution across vast infrastructures
- Cross-platform support including Linux, Windows, Mac OS X, and UNIX
- Self-healing capabilities that automatically detect and resolve outages
Cons:
- Steep learning curve for newcomers
- High resource consumption affecting performance
- Complex debugging requiring deep knowledge of Salt internals
- Limited web UI capabilities through Halite
SaltStack Pricing
SaltStack offers a free open-source version plus enterprise pricing at approximately $150 per machine annually. The acquisition by VMware in 2020 has brought enhanced support options but raised questions about potential price adjustments.
SaltStack Best Use Cases
SaltStack excels for organizations managing large-scale distributed IT environments. It performs particularly well in security compliance automation and self-healing infrastructure scenarios. Teams requiring comprehensive infrastructure management across multiple frameworks might consider platforms like env zero, which provides unlimited concurrency and broader tool support.
Checkov
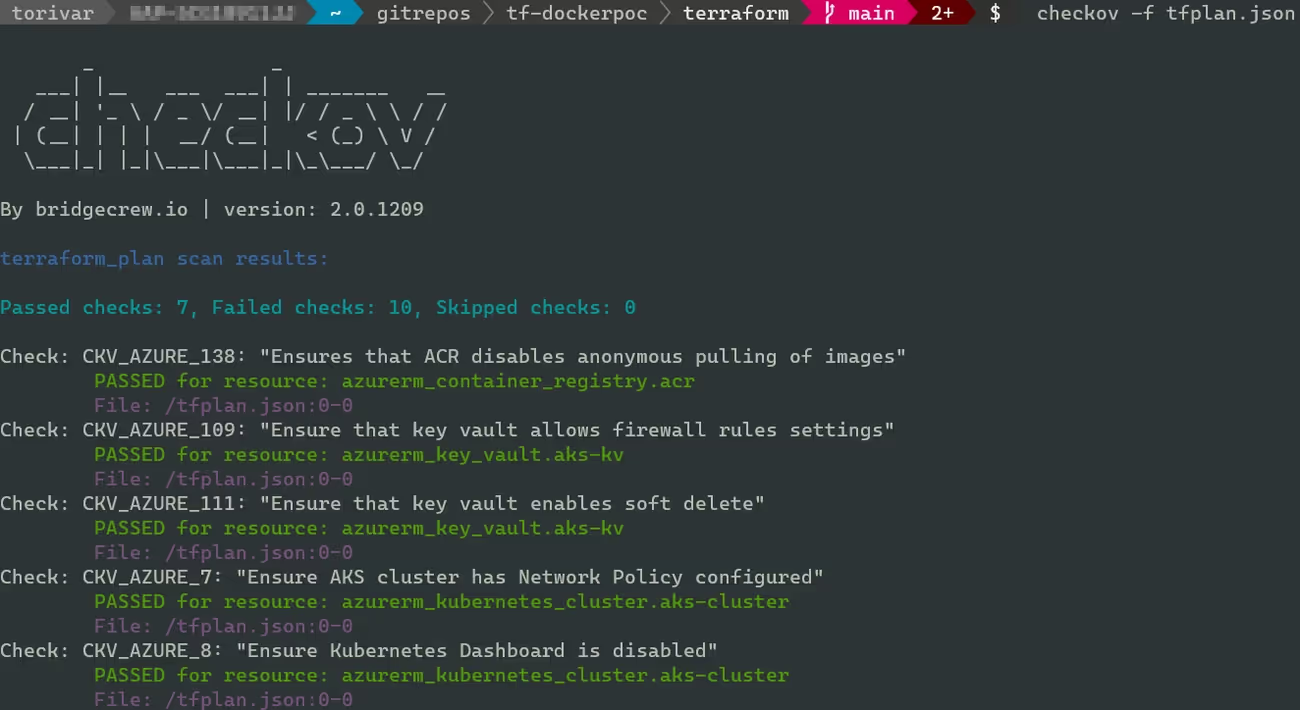
Image Source: Torivar
Checkov operates as an open-source static code analysis tool that identifies security risks and compliance violations in infrastructure as code before deployment. Developed by Bridgecrew and now part of Palo Alto Networks, this security-focused tool has been downloaded over 80 million times since launching in 2019.
What Makes Checkov Distinctive for Security Analysis?
Checkov employs graph-based scanning that provides context-aware security analysis across resources and their dependencies. The tool supports multiple IaC frameworks including Terraform, CloudFormation, Kubernetes, Helm, ARM, Bicep, and Dockerfiles. With over 3,000 customizable policies, Checkov covers more than 50% of configurations for most CIS Benchmarks.
Key security capabilities include:
- Deep Terraform scanning with module dependency resolution
- Secret detection for exposed credentials and API keys
- Multiple output formats including JSON, CSV, SARIF, and GitHub Markdown
- Baseline feature allowing teams to skip existing misconfigurations while enforcing standards for new code
How Does Checkov Address Infrastructure Security Challenges?
Strengths:
- Framework coverage across diverse infrastructure environments
- Zero cost as completely open-source software
- Extensive integrations with CI/CD tools including GitHub Actions, GitLab CI, and VS Code
- Policy customization through Python or YAML
Limitations:
- Focuses solely on static analysis without runtime security monitoring
- Requires integration with other tools for complete infrastructure governance
- Policy management complexity increases with scale
When Should Teams Consider Checkov?
Checkov works best for organizations prioritizing security compliance in their infrastructure as code workflows. Teams implementing shift-left security practices find Checkov valuable for catching misconfigurations before they reach production environments. The tool integrates effectively with existing development workflows, providing immediate feedback on security violations during code review processes.
For organizations seeking security analysis alongside broader infrastructure automation capabilities, env zero provides policy enforcement integrated with multi-framework deployment workflows, offering both security governance and operational efficiency.
How Do These IaC Tools Compare Across Key Dimensions?
Understanding the practical differences between IaC tools requires evaluating them across consistent criteria that matter for infrastructure operations. The comparison below highlights essential capabilities, pricing models, and trade-offs that influence tool selection decisions. Use this framework to match organizational requirements with platform strengths, recognizing that no single tool excels in every dimension.
Decision factors emerge from this comparison: teams managing multiple IaC frameworks benefit from platforms like env zero that provide unified workflows, while organizations committed to single cloud providers can optimize with native tools. The pricing models reveal different cost structures—resource-based billing versus environment-based pricing—that affect budget predictability at scale. Security and compliance requirements may favor tools with built-in policy enforcement and audit capabilities over those requiring additional integration work.
Key Takeaways
These expert insights will help you select the right IaC tool for your cloud automation needs in 2026:
• Multi-framework platforms like env zero offer unlimited concurrency and comprehensive governance, making them ideal for teams with varying expertise levels across complex infrastructures.
• Terraform remains the market leader with 32.8% share, but recent license changes have sparked alternatives like OpenTofu for organizations prioritizing open-source freedom.
• Programming language-based tools like Pulumi enable 80-90% deployment time reductions by allowing teams to apply mature software development practices to infrastructure.
• Cloud-native solutions (CloudFormation, Bicep, CDM) excel within their ecosystems but limit multi-cloud flexibility, while Kubernetes-native Crossplane offers continuous reconciliation.
• Security-first approaches are critical as 73% of enterprises face AI-related incidents, with tools like Checkov providing essential static analysis before deployment.
The IaC market's explosive 24% annual growth reflects infrastructure automation's strategic importance. Success depends on matching tool capabilities to your team's expertise, infrastructure complexity, and governance requirements. Organizations managing diverse environments benefit most from platforms supporting multiple frameworks with robust cost controls and self-service capabilities.
Frequently Asked Questions/FAQs
What is the most versatile Infrastructure as Code (IaC) tool for multi-cloud environments?
Terraform is widely considered the most versatile IaC tool for multi-cloud environments. It supports multiple cloud providers, uses a declarative language (HCL), and excels at managing complex infrastructure across different platforms.
How does env zero differ from other IaC tools?
env zero stands out by offering multi-framework support, including Terraform, OpenTofu, and Pulumi, with unlimited concurrent deployments. It provides comprehensive cost controls, self-service capabilities with guardrails, and is particularly valuable for teams with varying levels of expertise.
What are the advantages of using Pulumi for infrastructure automation?
Pulumi allows teams to define infrastructure using general-purpose programming languages like Python and TypeScript. This approach can lead to 80-90% reductions in deployment time by applying mature software development practices to infrastructure management.
Which IaC tool is best for organizations primarily using AWS?
AWS CloudFormation is the native IaC tool for AWS environments. It offers deep integration with all AWS services, automatic rollback on failure, and built-in state management without additional costs beyond the AWS resources used.
How does Checkov enhance security in IaC deployments?
Checkov is an open-source static code analysis tool that identifies security risks and compliance misconfigurations in IaC before deployment. It supports multiple frameworks, offers over 3,000 customizable policies, and provides context-aware security analysis across resources and modules.

.webp)