
IaC drift detection identifies when actual cloud infrastructure diverges from the state defined in your Infrastructure as Code configuration files, creating gaps that affect security, compliance, and operational reliability. When your infrastructure's current state differs from your coded IaC definitions, engineering teams operate against an outdated blueprint while live systems run configurations that no longer match the documented architecture. This misalignment becomes progressively more dangerous as it accumulates, degrading security posture, performance predictability, and compliance adherence.
Infrastructure drift commonly originates from emergency fixes or temporary adjustments made directly through cloud consoles or CLI tools that never get captured back into IaC configuration files. These undocumented modifications create operational hazards for teams depending on configuration consistency and reproducible deployments. Despite increased adoption of specialized tools for cloud infrastructure drift identification, approximately 20% of organizations report they cannot detect drift effectively across their environments. Robust IaC drift detection processes become essential rather than optional—preventing carefully architected infrastructure from silently degrading through untracked changes.
This guide examines practical detection techniques, prevention strategies, and remediation workflows that maintain alignment between your IaC definitions and actual cloud resources. You will learn native tool capabilities and their limitations, automated monitoring approaches that integrate with CI/CD workflows, and decision frameworks for choosing between manual and automated remediation strategies based on severity, scale, and compliance requirements. If you are looking for how to specifically detect and remediate Terraform drift, check out our Ultimate Guide to Terraform Drift Detection.
Understanding Infrastructure Drift in IaC
Infrastructure drift represents a fundamental challenge in modern cloud operations, affecting approximately 90% of large-scale IaC deployments with nearly half of these cases remaining undetected. This silent divergence creates operational risks that compound over time as the gap between intended and actual configurations widens.
How Does IaC Drift Differ from Configuration Drift?
Infrastructure drift in IaC describes the discrepancy between live cloud resources and the state defined in your IaC configuration files, occurring when actual infrastructure deviates from coded definitions. Configuration drift focuses on parameter misalignments within existing cloud services rather than structural resource differences.
This distinction affects remediation strategies: infrastructure drift typically involves entire resources created or deleted outside IaC workflows, while configuration drift concerns attribute changes like modified security group rules or altered encryption settings. Infrastructure drift carries broader implications because it affects the foundational architecture of your environment, potentially creating resource orphans or dependency breaks that configuration drift alone cannot produce.
What Is the Relationship Between Desired State and Actual State?
The IaC model establishes desired state as the infrastructure configuration specified in your files like Terraform's .tf definitions, serving as the authoritative blueprint for resource creation, modification, and deletion. This desired state includes resource properties, dependencies, and settings that define your intended architecture.
Actual state represents the real-world configuration of your cloud resources at any given moment. Initially, applying IaC configurations creates alignment between these states, but manual changes and external factors gradually introduce divergence.
IaC platforms manage this relationship through state files that track current infrastructure configurations. Terraform maintains its understanding in the terraform.tfstate file, updating this record with each apply operation. When drift occurs, the state file becomes stale relative to actual cloud resources, creating the foundation for detection and remediation workflows.
What Are Common Examples of Infrastructure Drift?
Infrastructure drift manifests across multiple dimensions in cloud environments:
Resource modification patterns:
- Security group rules modified to allow broader IP ranges or additional ports for testing that remain permanently opened
- Instance types upgraded during traffic spikes (t2.micro to m5.large) without corresponding IaC updates
- IAM policies expanded from read-only to full permissions through simple wildcard additions
Storage and data configuration changes:
- S3 buckets manually changed from private to public access for temporary requirements but left exposed
- Database instance types upgraded to handle load increases (db.m5.xlarge to db.m5.4xlarge) without cost impact analysis
Systemic drift sources: Cloud provider automatic updates, third-party management tools operating outside IaC workflows, and overlapping configurations from multiple teams create additional drift vectors. These changes often appear minor initially but cascade into significant operational issues affecting security posture, compliance adherence, performance characteristics, and cost efficiency.
Understanding these drift patterns enables teams to implement targeted prevention strategies and prioritize detection efforts based on risk profiles and organizational impact.
What Causes IaC Drift and How Does It Impact Your Infrastructure?
Understanding the root causes of infrastructure drift enables teams to implement targeted prevention strategies before misalignment creates operational problems. Common causes include manual edits through cloud consoles, overlapping IaC configurations across teams, external automation operating outside defined workflows, and state file inconsistencies. Each cause creates different operational impacts that affect security, compliance, and deployment reliability.
What Role Do Manual Changes Play in Creating Infrastructure Drift?
Direct human intervention through cloud provider interfaces represents the most frequent source of infrastructure drift, accounting for nearly 90% of drift cases. This pattern, often referred to as ‘ClickOps,’ emerges from three primary scenarios that teams encounter repeatedly.
First, emergency response situations drive engineers to bypass IaC workflows during high-severity incidents or outages. Increasing instance capacity during traffic spikes, modifying security groups during security events, or adjusting database configurations during performance issues solve immediate problems but create divergence when these changes never get backported into IaC definitions. The business pressure to resolve incidents quickly often overrides proper change documentation processes. Second, process complexity creates friction that encourages shortcuts. When implementing minor adjustments requires navigating lengthy approval workflows or complex CI/CD pipelines, practitioners frequently choose direct console modifications over following established procedures. This trade-off between operational speed and configuration consistency becomes particularly problematic in organizations where IaC processes haven't been optimized for developer productivity.
Finally, access control gaps enable unauthorized modifications that compound drift over time. Without proper role-based access control (RBAC) and least-privilege enforcement, team members can alter resources outside established IaC channels, creating environments that become increasingly unpredictable and difficult to reproduce.
How Do Overlapping IaC Configurations Create Persistent Drift?
Multiple teams managing overlapping resources creates systematic drift that persists across deployment cycles. This problem manifests through resource ownership ambiguity and tool migration complexities.
Resource boundary confusion occurs when stack definitions overlap, particularly in large organizations where infrastructure management spans multiple teams and evolves over extended periods. Competing configurations managing the same cloud assets create conflicts that generate drift as different teams apply their respective IaC definitions.
Tool migration periods introduce additional complexity when organizations evolve their IaC practices by switching platforms—from CloudFormation to Terraform, for example. During transition phases, resources exist in multiple configuration systems simultaneously, creating parallel management paths that can inadvertently overwrite each other's changes and establish persistent drift cycles.
How Does External Automation Contribute to Infrastructure Drift?
Significant infrastructure divergence occurs through automation operating outside IaC workflows, creating systematic drift that teams often discover only during planned deployments.
Automated emergency response systems implement "shadow fixes" that modify cloud resources directly without updating corresponding IaC code. These systems resolve immediate operational problems but establish long-term infrastructure inconsistencies because their changes remain invisible to IaC tools and team members reviewing configuration definitions.
Legacy automation routines continue modifying infrastructure independently of current IaC management. Older cron jobs, scheduled tasks, or monitoring systems might make regular changes to resources now under IaC control, creating recurring drift patterns that can be difficult to trace back to their automation sources.
Third-party management tools that interface directly with cloud providers often bypass IaC processes entirely. Each modification of these tools increases deviation between defined and actual states, presenting particular challenges for organizations using multiple IaC tools that operate without awareness of each other's changes.
What Infrastructure Issues Create Drift Without Direct Intervention?
Some drift develops without human or external automation involvement, stemming from cloud provider behaviors and IaC tool limitations.
Cloud providers regularly implement automatic updates to their services, sometimes modifying default settings, resource behaviors, or API responses. When IaC configurations don't get refreshed to accommodate these provider changes, drift accumulates as actual resource configurations diverge from what IaC tools expect.
State file problems represent a critical source of infrastructure drift that affects IaC tool accuracy. These files track relationships between IaC code and deployed resources, and when they become corrupted, deleted, or desynchronized, IaC tools lose their ability to map code to actual infrastructure accurately.
State locking failures in team environments create significant drift risks during concurrent operations. Without proper locking mechanisms, simultaneous operations by multiple team members can corrupt state files, causing Terraform or similar tools to lose track of actual resource conditions. When two engineers run terraform apply simultaneously, one operation might overwrite the other's changes, leading to state file corruption and systematic resource mismanagement that propagates across subsequent deployments.
What Are the Business Consequences of Unmanaged IaC Drift?
"Some industries like financial services and healthcare cannot tolerate infrastructure drift. Automated detection becomes a regulatory requirement, not just operational best practice." — Dev.to Community, Terraform and compliance experts
Unaddressed infrastructure drift creates operational risks that extend well beyond technical inconvenience, affecting security posture, regulatory compliance, performance reliability, and deployment processes. The consequences of persistent drift in production environments cascade through multiple organizational layers, creating compounding problems that become increasingly difficult to resolve over time.
How Does Infrastructure Drift Create Security Vulnerabilities?
Left unchecked, IaC drift frequently opens security gaps that attackers can exploit. Silent configuration changes often introduce backdoors or expose resources unintentionally. The 2020 Twilio breach demonstrates these risks—configuration drift in an S3 bucket allowed attackers to access users' personal data for years before detection. Even seemingly minor adjustments, such as security group rules temporarily modified for testing, can grant unintended public access that persists long after the original need expires.
These security vulnerabilities stem from the gap between documented and actual configurations. When security policies exist only in IaC code but actual resources run with different settings, security teams operate with incomplete visibility into their attack surface. Emergency fixes applied directly to cloud consoles bypass security reviews that would normally catch misconfigurations, creating persistent exposure that security monitoring may not detect.
Why Do Undocumented Changes Lead to Compliance Failures?
Undocumented infrastructure modifications create regulatory challenges that auditors cannot ignore. Changes not captured in your IaC repository become invisible to compliance processes, creating gaps that generate violations of regulations including GDPR, HIPAA, and PCI. To an auditor, invisible infrastructure is untrustworthy infrastructure. These violations carry immediate financial consequences and can trigger extended audit periods that consume significant resources.
The compliance risk intensifies because drift makes it impossible to prove that your infrastructure meets regulatory requirements at any given time. Audit teams must manually trace configuration changes through multiple tools and interfaces, increasing both the time and stress associated with security audits. Organizations lose the ability to demonstrate continuous compliance, forcing reactive rather than proactive compliance management.
How Does Drift Degrade Performance and Increase Costs?
Unmanaged infrastructure drift typically produces operational inefficiencies that compound over time. Drifted configurations create uneven workload distribution across load-balanced servers, causing some systems to become overloaded while others remain underutilized. Improperly configured caching mechanisms or database settings significantly degrade application performance. These issues accumulate, creating inconsistent environments that experience unpredictable failures and increased downtime.
Cost implications prove equally problematic. Drift usually results in unnecessary resources or misconfigured settings that increase cloud expenses while simultaneously degrading performance. Teams lose visibility into resource optimization opportunities because actual configurations no longer match cost models based on IaC definitions. The combination of performance degradation and cost increases creates a double impact on operational efficiency.
What Impact Does Drift Have on CI/CD Pipeline Reliability?
Configuration differences between environments create mysterious deployment failures that disrupt release processes. When staging environments (where tests pass) differ from production environments (where deployments fail), teams encounter failures that seem impossible to reproduce. This environmental drift often results from manual changes or incomplete Infrastructure as Code coverage. Pipeline inconsistencies make tests unreliable and slow release velocity dramatically.
Engineers spend increasing time firefighting environment issues rather than delivering features, creating a breakdown in release pipeline reliability that affects overall infrastructure dependability. The operational overhead of managing drift-related deployment failures reduces team productivity and increases the risk of rolling back releases due to environment-specific problems rather than code issues.
How Can You Detect IaC Drift Across Different Platforms?
Each Infrastructure as Code platform provides distinct methods for identifying misalignments between your defined configurations and actual cloud resources. Effective drift detection requires understanding both the capabilities and limitations of these native tools, along with when to supplement them with automated monitoring platforms.
Native Terraform Commands for Drift Detection
Terraform's terraform plan command serves as the primary method for surfacing infrastructure drift by comparing your current state file against actual cloud resources and highlighting discrepancies. The process involves Terraform refreshing its understanding of real-world resource states, then contrasting this information against your configuration files to identify any deviations.
A straightforward example: if an S3 bucket's versioning setting was manually changed from enabled to disabled, terraform plan would detect this drift and propose reverting it to match your code. The command generates a detailed report showing exactly what changes would occur if you applied your configuration again.
Native Terraform workflow for drift detection:
- Run
terraform refreshto update state from provider APIs - Execute
terraform planto compare configuration against current state - Review the output for any unexpected changes or modifications
The limitations are practical: this approach cannot detect drift in resources not managed by Terraform, lacks support for planning across multiple state files, and requires manual execution or integration with CI/CD workflows for regular monitoring. To learn how to specifically detect and remediate Terraform drift, check out our Ultimate Guide to Terraform Drift Detection.
AWS CloudFormation Drift Detection Capabilities
CloudFormation provides built-in drift detection accessible through both the AWS console and CLI, beginning with the detect-stack-drift command that initiates comparison between your stack template and deployed resources.
The detection workflow follows a structured three-step process:
- Execute
detect-stack-drift --stack-name <stack-name>to start detection - Monitor progress using
describe-stack-drift-detection-status - View detailed results with
describe-stack-resource-drifts
CloudFormation drift detection operates strictly on-demand, requiring explicit triggering rather than providing continuous monitoring. Teams needing automated regular checks must implement custom solutions using EventBridge, Lambda functions, or AWS Config rules.
Pulumi's Drift Detection Through Preview Commands
Pulumi enables drift detection via its pulumi preview --refresh command, which compares current cloud resource states against what Pulumi expects based on your code definitions. Running pulumi preview --refresh --stack <STACK NAME> produces a detailed list of proposed changes, clearly identifying resources that have drifted from their intended configuration.
This command can detect modifications such as manually altered EC2 instance tags or changed user data that occurred outside Pulumi's management. Pulumi Cloud extends this capability by offering scheduled drift detection that automatically executes these operations on a regular cadence and notifies teams when discrepancies emerge.
GitOps-Based Detection with ArgoCD and FluxCD
ArgoCD implements drift detection following GitOps principles through continuous monitoring of both Git repositories and deployed Kubernetes resources. When discrepancies arise between these states, ArgoCD marks applications as OutOfSync, providing visual representations of configuration drift.
This approach offers clear highlighting of differences between desired and actual configurations while enabling both manual reconciliation and automatic synchronization to eliminate drift in Kubernetes environments. The GitOps model ensures that Git remains the single source of truth for infrastructure state.
Automated Platform Solutions: env zero’s Approach
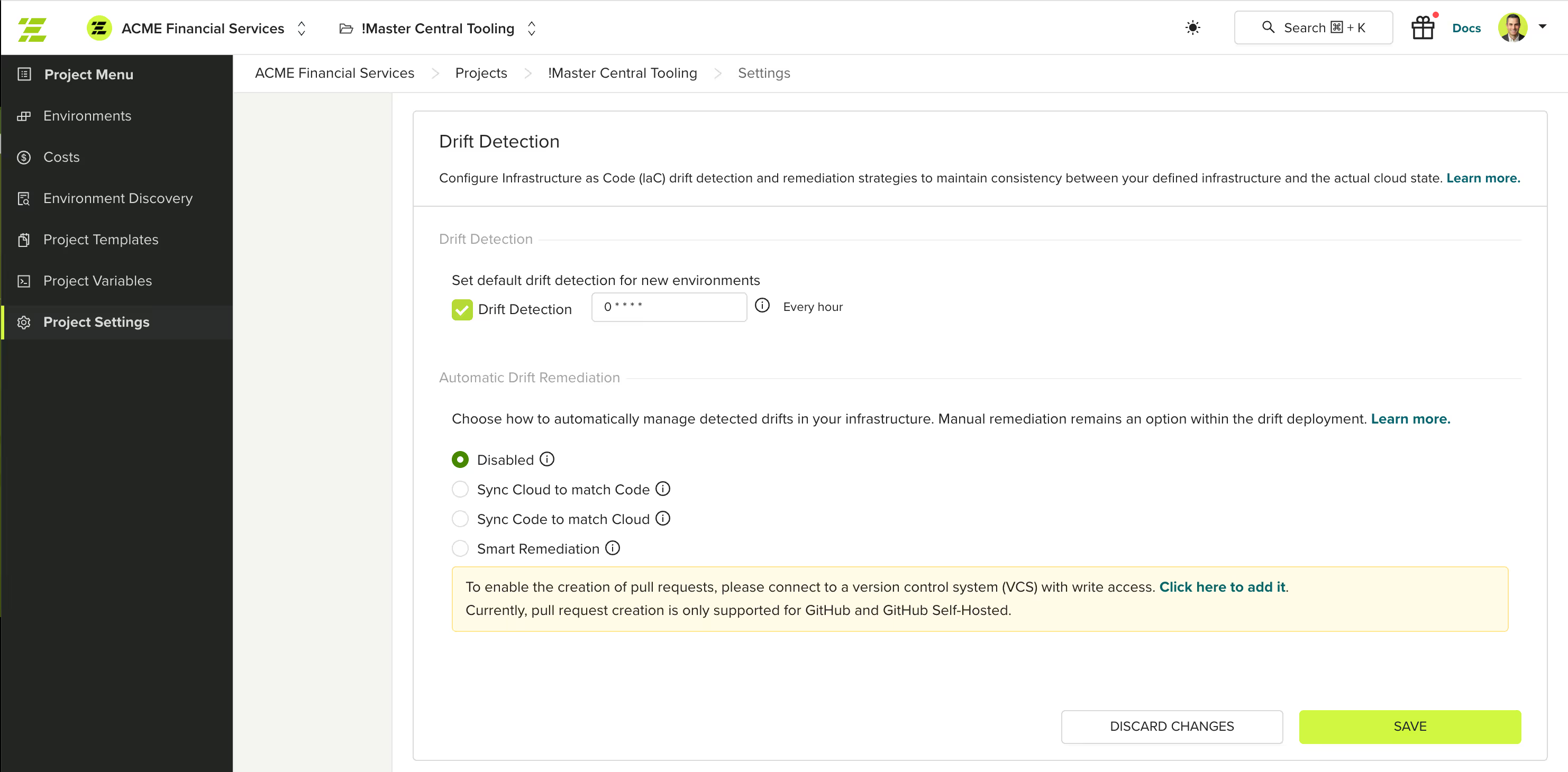
env zero automates drift detection and remediation through scheduled scans that regularly compare infrastructure against IaC definitions, recognizing that drift can occur at any time and making continuous monitoring essential. The platform executes proposed runs in the background and flags affected resources with visible indicators when drift is detected.
env zero’s automated approach includes:
- Background execution of drift detection scans
- Clear visual flagging of drifted resources
- Automatic triggering of reconciliation jobs when configured in either a code-to-cloud, cloud-to-code, or Smart Remediation mode (If the drift comes from the cloud, create a pull request; f the drift comes from the code, apply the changes via env zero deployment)
These capabilities extend native tool functionality by providing scheduling, centralized reporting, and integration with approval workflows that scale across multiple environments and teams.
The choice between native tools and automated platforms depends on team size, compliance requirements, and the frequency of infrastructure changes across your environments.
How Do You Remediate IaC Drift Efficiently?
Remediation begins with assessing drift severity and impact, deciding whether to update code, revert manual changes, or reconcile through guided workflows, and then executing with appropriate governance and audit controls. The choice between manual and automated remediation depends on factors including drift severity, organizational scale, and compliance requirements. Below we examine specific remediation techniques and their appropriate applications.
What Are the Core Remediation Strategies for Different Drift Types?
After identifying drift through detection tools, terraform apply provides the most direct path to reconcile discrepancies by reverting external changes to match your IaC definitions. Terraform compares current state with configuration files and makes necessary adjustments to restore alignment. For instance, if security group rules were manually modified outside IaC workflows, terraform apply restores them to match your coded configuration.
However, not all drift requires reverting to code. Manual changes that represent legitimate improvements should be preserved by backporting modifications to your IaC definitions. This process involves examining drift reports to understand what changed, updating configuration files to incorporate valid modifications, and validating changes through terraform plan or tofu plan (for OpenTofu) to confirm no further differences exist.
For resources created entirely outside IaC workflows, the terraform import command brings them under proper management. This restoration process follows three steps: write corresponding Terraform code for existing resources, use terraform import <resource_address> <resource_ID> to map actual resources to code, and verify alignment through terraform plan. This technique proves particularly valuable for recovering control over resources created through cloud consoles or emergency CLI modifications.
What is the Best Remediation Approach to Handle Drift?
Your organization’s remediation approach selection depends on several decision factors:
- Severity: Security or regulatory drift requires fast, controlled remediation with approval workflows.
- Scale: Widespread drift across multiple resources favors automated reconciliation tools.
- Auditability: Compliance requirements favor tracked, approved remediation with detailed audit logs.
These factors guide teams toward manual inspection for critical changes, guided workflows for moderate-scale drift, and automated reconciliation for routine configuration misalignments.
IaC drift detection represents a foundational practice for maintaining infrastructure integrity in cloud environments. This guide has explored detection techniques ranging from native tool commands to automated monitoring platforms, prevention strategies that reduce drift through policy-as-code and access controls, and remediation approaches that balance speed with governance requirements. The business consequences—security vulnerabilities, compliance violations, performance degradation, and deployment failures—make drift detection essential rather than optional for teams managing cloud infrastructure at scale.
Effective drift management combines appropriate tooling with consistent operational processes. Native commands like terraform plan and CloudFormation's drift detection provide immediate troubleshooting capabilities but require automation platforms for continuous monitoring and centralized governance. Prevention strategies through policy enforcement, RBAC, and immutable infrastructure patterns reduce drift frequency, while remediation frameworks help teams decide between reverting changes, updating code, or automated reconciliation based on severity and compliance requirements.
Decision factors for implementation:
- Detection approach: Continuous monitoring for large-scale environments; on-demand scanning for focused troubleshooting.
- Prevention controls: Policy-as-code enforcement and access controls to reduce manual modification opportunities.
- Remediation strategy: Automated reconciliation for low-risk drift; approval workflows for security-critical changes.
Teams implementing robust drift detection workflows protect their infrastructure investments from gradual degradation while maintaining the reliability and security that stakeholders expect. Modern tooling makes continuous monitoring achievable across environments of varying complexity, enabling organizations to preserve the architectural integrity their systems depend on for operational success.
Frequently Asked Questions/FAQs
What is infrastructure drift in IaC?
Infrastructure drift occurs when the actual state of your cloud resources deviates from the desired state defined in your Infrastructure as Code (IaC) configuration files. This misalignment can lead to security vulnerabilities, compliance issues, and operational problems.
How can I detect infrastructure drift?
You can detect infrastructure drift using various tools and techniques. For Terraform, use the 'terraform plan' command. AWS CloudFormation offers drift detection via CLI. Pulumi provides the 'pulumi preview --refresh' command. Some platforms like env zero offer automated, scheduled drift scans and alerts.
What are the risks of unmanaged infrastructure drift?
Unmanaged infrastructure drift can lead to security vulnerabilities from misconfigured resources, compliance failures due to undocumented changes, performance degradation, resource overprovisioning, and deployment failures in CI/CD pipelines.
How can I remediate infrastructure drift?
To remediate drift, you can use 'terraform apply' to restore the desired state, update your IaC code to reflect valid manual changes, use 'terraform import' for missing resources, leverage drift-aware change sets in AWS CloudFormation, or implement automated reconciliation with platforms like env zero.
Why is regular drift detection important?
Regular drift detection is crucial because it helps maintain the integrity of your infrastructure, prevents security vulnerabilities, ensures compliance, maintains performance, and avoids deployment failures. It safeguards your infrastructure investment from gradual degradation and potentially catastrophic changes.

.webp)




