Best Terraform Cloud Alternative
Cut infrastructure management costs, go beyond IaC, and avoid vendor lock-in with env zero.
env zero gives you broader governance and control than Terraform Cloud — including policy-as-code with OPA, multi-tool support, cost-aware workflows, and predictable pricing without per-resource charges. Manage infrastructure at scale with visibility, flexibility, and confidence.
Western Union

Join the companies modernizing infrastructure with env zero
env zero vs. Terraform Cloud at a glance

No vendor lock-in
Open-source friendly
Self-hosting available
Locked into Terraform
Subject to HashiCorp’s BSL license
Terraform
OpenTofu
Terragrunt
Pulumi
and more
Only supports Terraform
Predictable pricing per apply or environment
Usage-based (RUM)
Pricy and unpredictable
Cloud resource visibility
Usage tracking
Advanced drift management
AI-driven diagnostics for infrastructure insights
Limited to Terraform runs only
No cloud visibility or analysis tools
Rich capabilities set
Approval flows
Cost controls
Policy-as-code
RBAC
Limited policy engine
No cost management
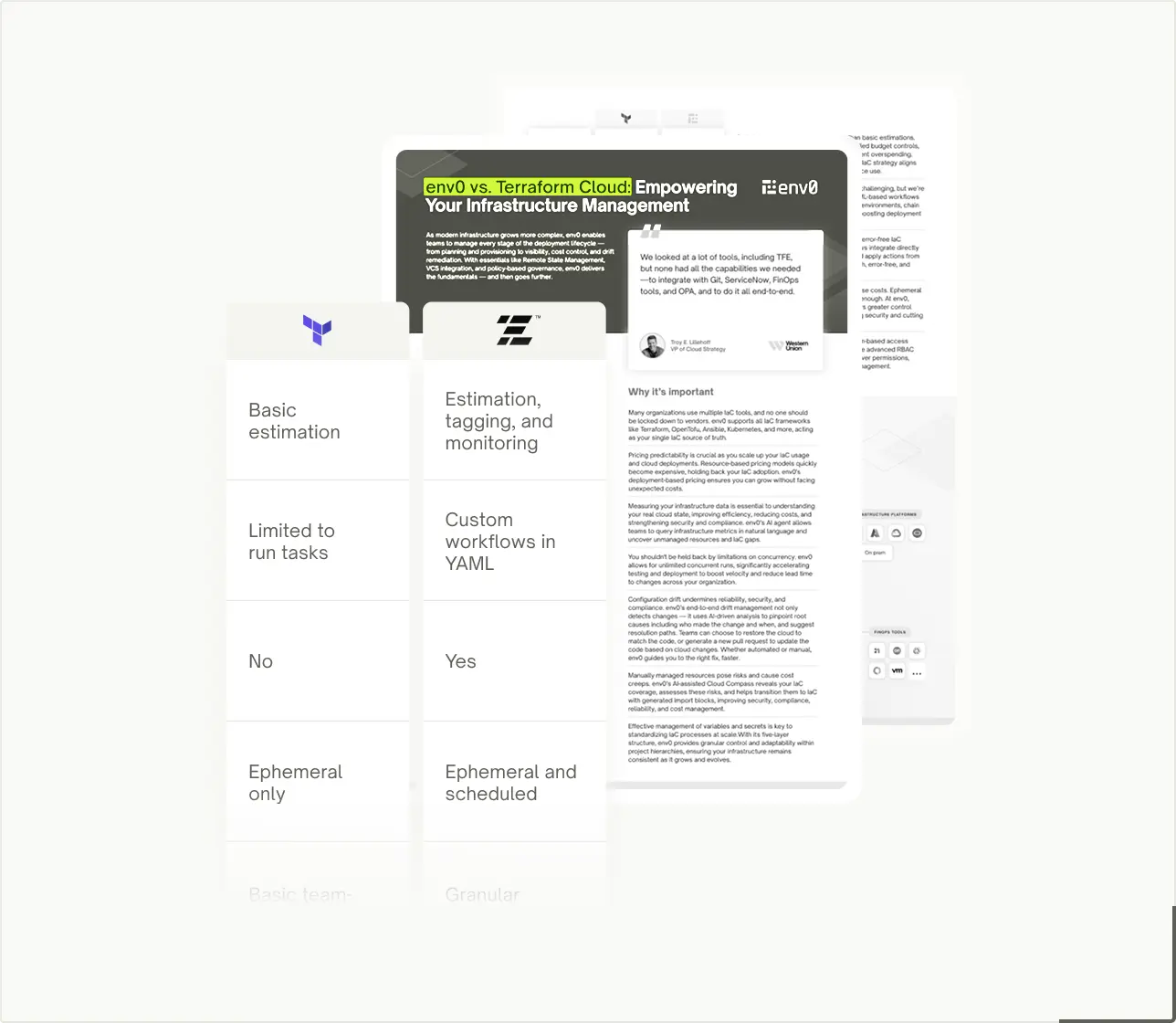
Compare env zero vs. Terraform Cloud
Download the free comparison guide to see why enterprises choose env zero
Here’s what happens when teams move to env zero
The env zero advantage
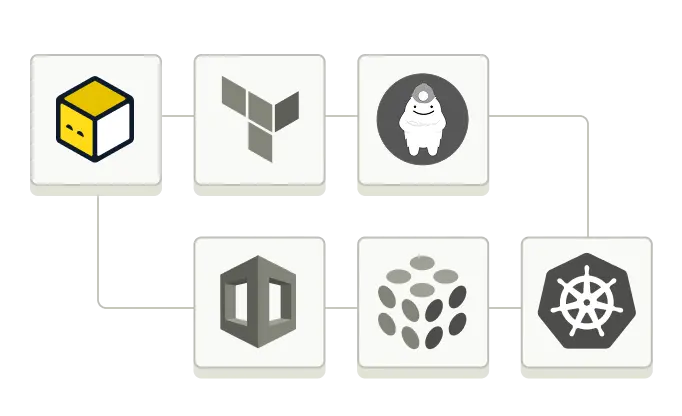
env zero supports every major Infrastructure-as-Code framework - including Terraform, OpenTofu, Pulumi, CloudFormation, and Kubernetes - so your teams can use what works best.
- Multi-framework and Kubernetes-native support
- Self-hosted agent for enterprise environments
- Integrates with your stack (Checkov, Grafana, DataDog, and more)
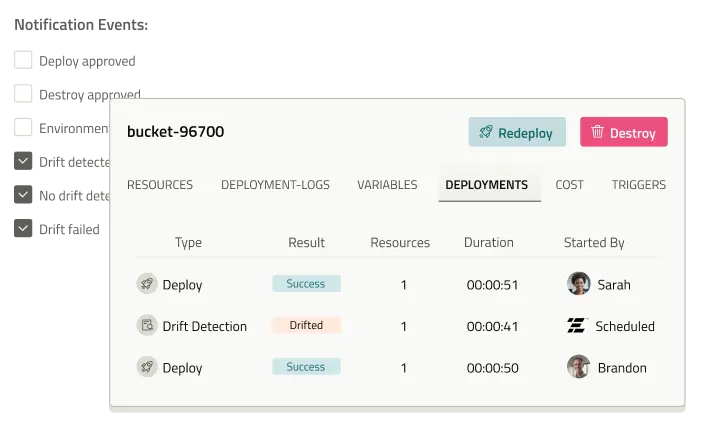
env zero enables you full visibility into your infrastructure and the automation to control it.
- Understand IaC coverage and drift risk across your cloud
- Measure and analyze infrastructure data with an AI-powered agent
- Detect and remediate drift with deep, audit-level precision
- Govern with advanced built-in approval flows, RBAC, and cost controls
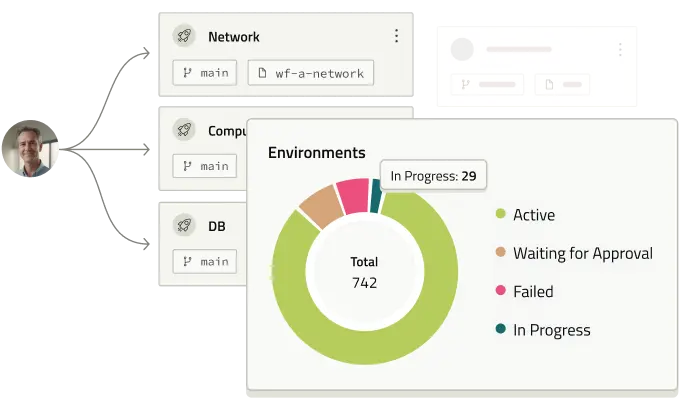
env zero is priced for scale - no resource-based billing, no vendor traps.
- Predictable pricing per environment, not per resource
- Unlimited concurrent deployments
- Flexible, customizable workflows
- Run as SaaS or host it yourself - your choice
Customer feedback matters most
Scale up benefits, cut down costs
Unlimited concurrency
Terraform Cloud's concurrent run fees can add up quickly. With env0, you can avoid wasteful spending and execute unlimited simultaneous runs at no extra cost.


IaC-centric pipelines
Replace Terraform Cloud webhooks with easy-to-use custom flows to seamlessly integrate whatever tools you may need. Leverage deployment workflows to easily manage multiple IaC stacks and resolve complex dependencies.


Flexible workflows
Teams have different needs and types of deployments with every project. env0 retains flexibility infrastructure teams need to make adjustments by using PR planning (with both git and Atlantis-style workflows), continuous deployment, and custom policies.


Managed self-service
Dismantle silos and regain valuable time with managed self-service tools and Policy-as-Code guardrails, empowering teams to spin up entire infrastructure with ease and confidence. Bake in IaC best practices with:


Advanced FinOps tools
With env0 you can easily monitor your spending, set custom budget policies, and automatically know the cloud costs of every change by using:


Robust IaC automation tools
CI/CD automation makes your Infrastructure as Code more manageable. Anchor IaC into your development lifecycle and detect issues before they hit production with:


Extended integration options
Unlike Terraform Cloud, env0 supports every Infrastructure-as-Code framework – Terraform, OpenTofu, Pulumi, CloudFormation, etc. Our platform also supports critical tools in the DevOps tech stack like:
- Kubernetes and Helm
- OPA and Checkov
- Trivy and Lightlytics
and many more


Continuous IaC visibility
Gain continuous visibility within your infrastructure stack, offering contextual insights into changes and drifts for granular auditability and compliance, enhanced by features like:


Granular access controls
Going beyond Terraform Cloud's static access controls, our platform supports dynamic RBAC and flexible access policies, streamlined by SAML/OIDC single sign-on (SSO) integrations.


What's new with env zero
.avif)














.avif)

















.svg)

.svg)



.svg)


.avif)


.svg)



.svg)


.avif)
