

Vendor lock-in is an important consideration when evaluating any technology. It's great when a tool or service is a perfect fit for your requirements, but over time product features, pricing models or your needs may change.
When that happens, you want to be sure that you can migrate to a new platform with minimal effort and zero impact. The newly released migration tool from env zero makes the migration process from Terraform Cloud to env zero simple, quick, and convenient.
Disclaimer
env zero is a Terraform Cloud competitor.
If you want to see how the two measure up, visit here to see what makes env zero a capable Terraform Cloud alternative.
Terraform Cloud Migration: Why migrate from Terraform Cloud?
Terraform Cloud is a Terraform automation platform offered by HashiCorp. It's an excellent service with a broad swath of happy users.
That being said, products and requirements change over time resulting in a mismatch of product and customer. Here are a few reasons we've heard of customers considering a migration:
- The Resources Under Management (RUM) pricing has driven up costs for the platform.
- The BSL license change caused uncertainty and some would like to stick with an open-source tool.
- There are new business requirements that are not met by the platform.
While it's not necessarily the main decision factor, the most common reason at the moment is the new RUM pricing model.
While it may work out advantageously for some organizations, others are structured in a way where the new pricing model causes costs to balloon. You can find a detailed analysis of Terraform Cloud pricing here.
Ultimately, if Terraform Cloud is working for you, then we are not suggesting that you migrate just for kicks. But if you find yourself looking to migrate off Terraform Cloud, the new env zero migration tool can make it easier for you and assist with moving your workspaces, including state and variables to env zero.
If you have more than a handful of Terraform workspaces in Terraform Cloud, migrating them to another platform manually is a time-consuming and error-prone process.
At a minimum, you need to create workspaces on the destination platform, copy over the settings and input variable values, and migrate the state data. That’s a daunting task to perform at scale, and so the env zero team created a migration tool to simplify and automate the migration process, reducing what could be days of tedious work to a few minutes of running scripts.
Getting started with the env zero migration tool
Born out of frequent customer requests, the migration tool simplifies and accelerates the transfer from Terraform Cloud to env zero, at any scale.
The tool is an open-source project available on GitHub. It is intended to migrate the contents of a Terraform Cloud workspace to an environment in env zero, including the following:
- Project placement
- VCS repository settings
- Terraform version value
- Variable values
- State data
The tool currently supports version control system (VCS) backed workspaces and will select OpenTofu on env zero if the workspace Terraform version on Terraform Cloud is 1.6 or newer.
Migration process
The migration process consists of a few simple stages: preparing your local machine, exporting Terraform Cloud workspace settings, and creating environments in env zero.
The tool follows the process outlined below:
- Prepare your local machine
- Export Terraform Cloud workspace settings
- Create environment in env zero with exported settings
- Copy state data from workspace to environment
You can migrate multiple Terraform Cloud workspaces at the same time and filter using tags. Let's walk through the process with some example workspaces in Terraform Cloud!
Note: The details of the migration process may change over time, refer to the README.md file in the GitHub repository for step-by-step instructions.
Prepare for Migration
On my local machine, I’ve cloned the GitHub repository containing the migration tool to a local directory. I’ve also procured API tokens from both Terraform Cloud and env zero.
On Terraform Cloud, I have three workspaces in a project called [.code]env0-migration-example[.code].
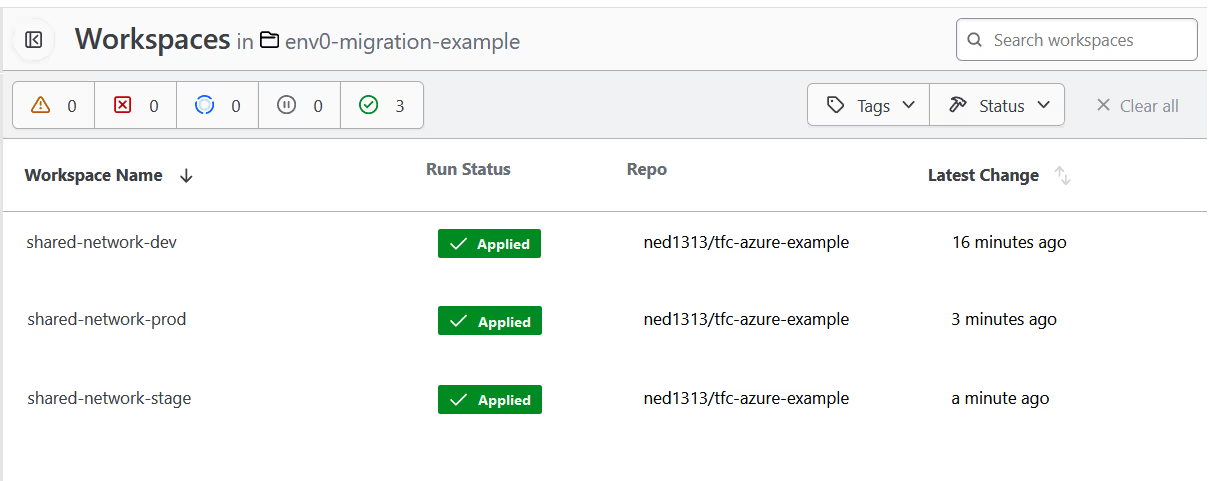
These are the workspaces we will be migrating to env zero. Looking in the details of one of the workspaces, it is using the VCS workflow linked to a public GitHub repository named [.code]tfc-azure-example[.code].
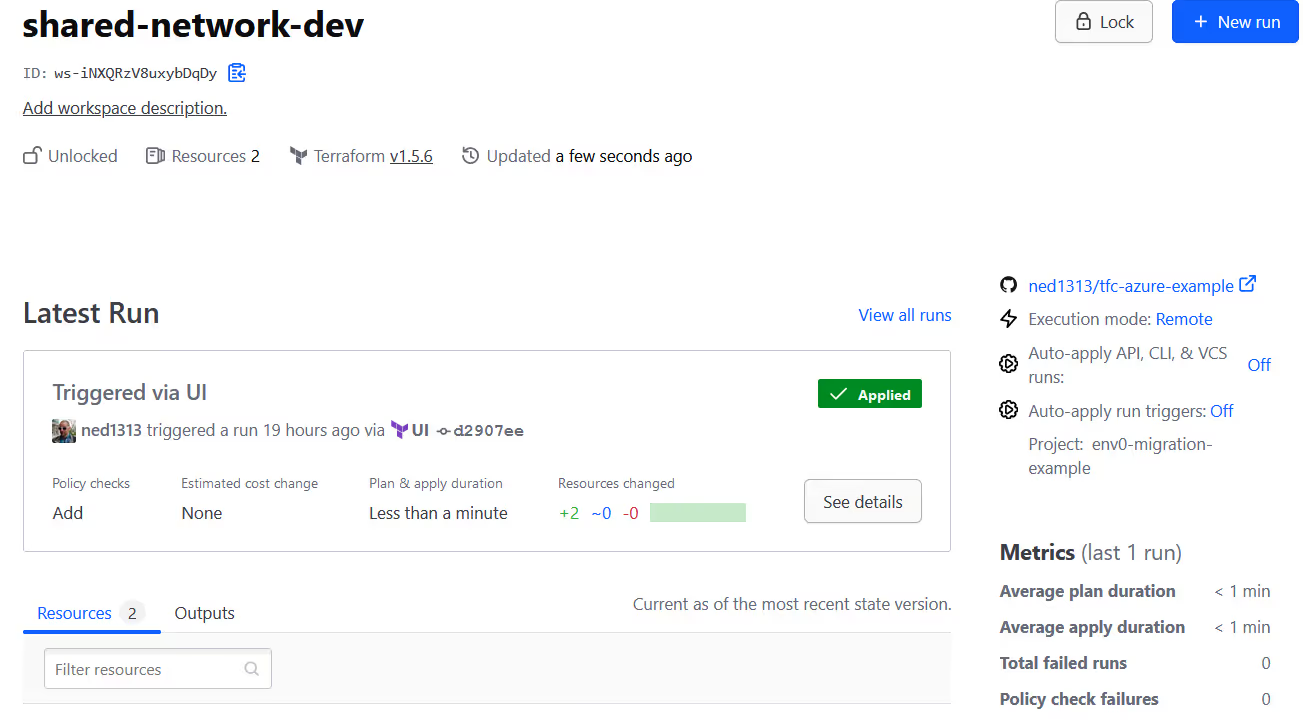
The workspace variables include a prefix value for naming and credentials for provisioning infrastructure in Azure.
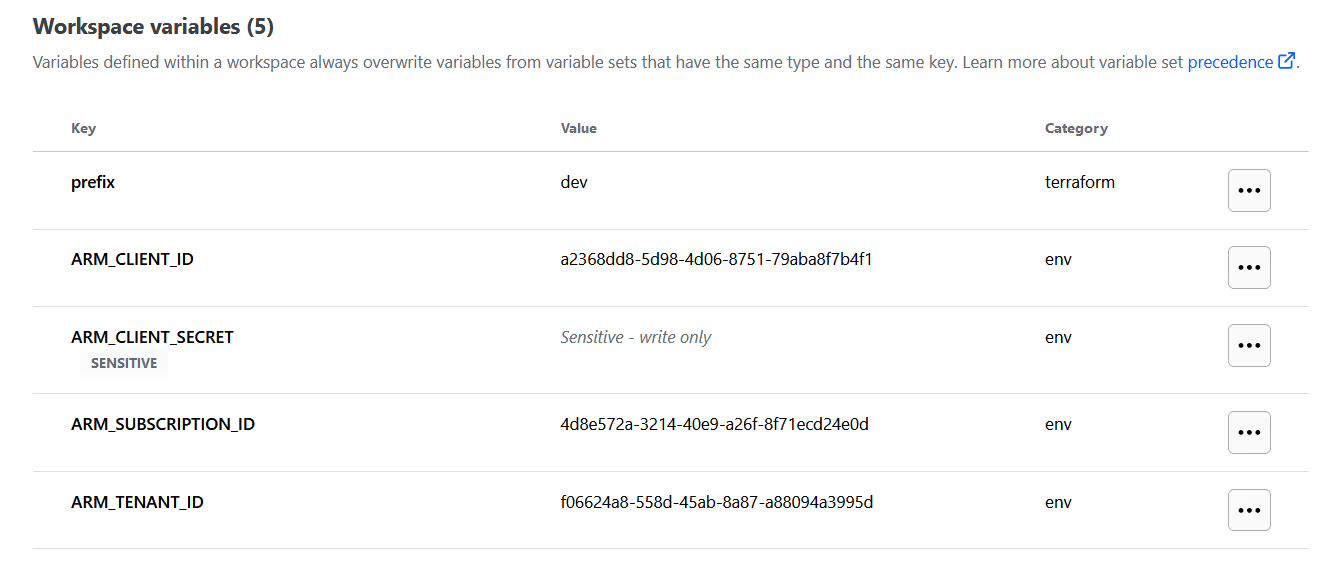
The migration process will migrate these variable values, the state data, and the workspace to env zero.
Export Terraform Cloud Workspaces and tfstate
Our first step is to export the Terraform Cloud workspaces we want to migrate using the Terraform configuration stored in the TFC directory of the cloned repository.
Before applying the configuration, we need to create a tfvars file with the following settings defined:
And set the environment variable TFE_TOKEN to our Terraform Cloud API token:
Now we can initialize the Terraform configuration and apply it.
Create environments in env zero
This step involves two processes... First, we will use the Terraform code in the env0-resources-generator directory to create a new Terraform configuration with all necessary resources for creating environments in our env zero account.
Then we’ll use the newly created configuration to actually deploy the resources to env zero.
Create a Terraform configuration for env zero
From the env0-resources-generator directory, we will run terraform init and apply, pointing to the data.json file for input:
The result is a collection of files in the env0-resources-generator/out directory that make up a Terraform configuration to deploy the corresponding projects and environments in env zero.
Deploy the env zero resources
Now that we have a configuration to deploy the necessary resources in env zero, we can navigate to the out directory and deploy it.
Before we run [.code]terraform apply[.code], we need to configure a couple environment variables to authenticate to env zero:
With those environment variables set, it’s a simple matter of navigating into the out directory and deploying the Terraform configuration:
When the deployment completes, we’ll now have a project with three environments deployed in env zero that mirrors our workspaces in Terraform Cloud.
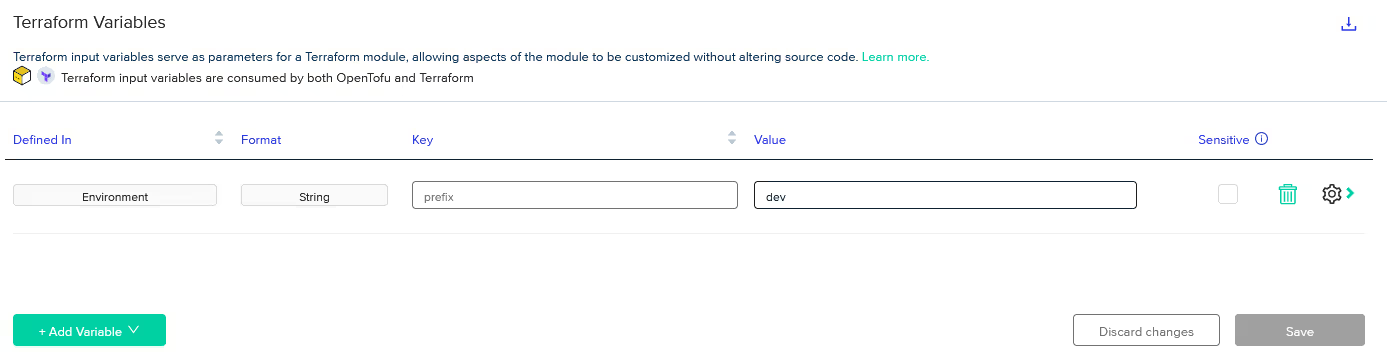
Looking inside the 'Variables' section of the [.code]shared-network-dev[.code] environment shows that both the Terraform and Environment variables have been copied over.
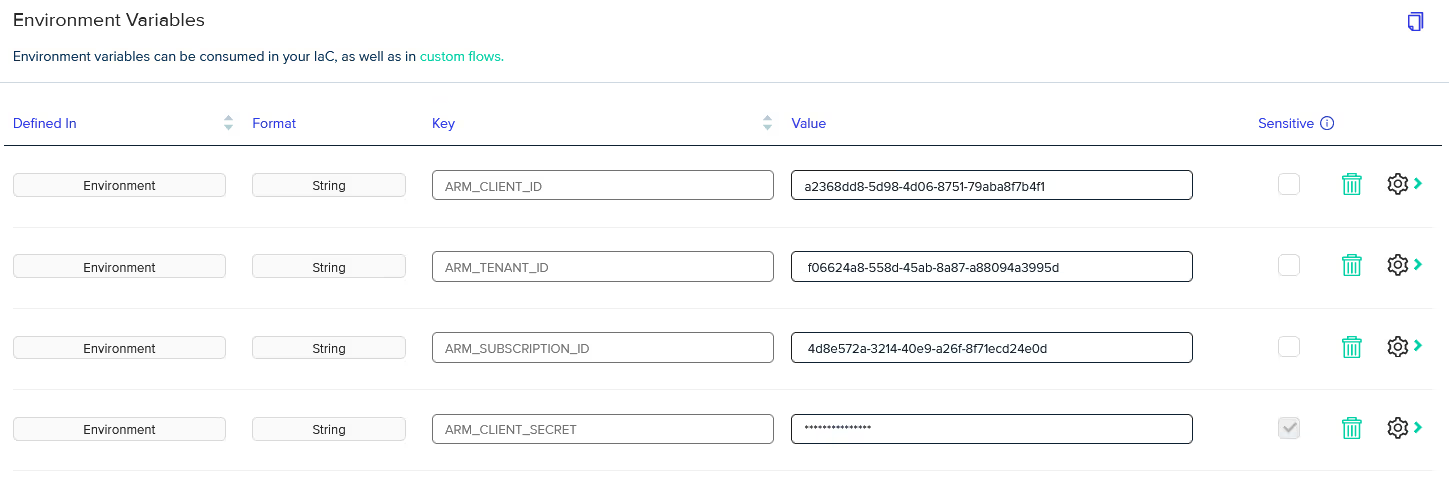
Since the [.code]ARM_CLIENT_SECRET[.code] was stored as sensitive in Terraform Cloud, the migration tool uses a placeholder value of [.code]secret_value_from_terraform_cloud[.code], which we need to update to the actual value.
The migration tool does not copy sensitive values to help prevent possible leakage and exposure on your local workstation. (Honestly, we should be using OIDC authentication anyway!)
Before we update the [.code]ARM_CLIENT_SECRET[.code] variable value, we still need to migrate the state data for our workspaces as well.
Copy terraform.tfstate data from workspace to environment
The state migration process uses the migrate_workspaces.sh bash script found in the TFC/migrate-state directory.
Before we run the script, we will need to set some additional environment variables:
The script also needs us to log into the Terraform Cloud and env zero backends using the [.code]terraform login[.code] command. First, we’ll generate a base64 token based on our env zero API credentials and use that value to log into the env zero backend:
Then log into Terraform Cloud using the token value stored in the [.code]TFC_TOKEN[.code] environment variable:
Once those prerequisites are met, we can run the script from the migrate-state directory:
The script will find the data.json file generated earlier and use its contents to migrate the state data for each workspace.
Looking at the State tab for the [.code]shared-network-dev[.code] environment, there is now an entry for the data we just copied over.
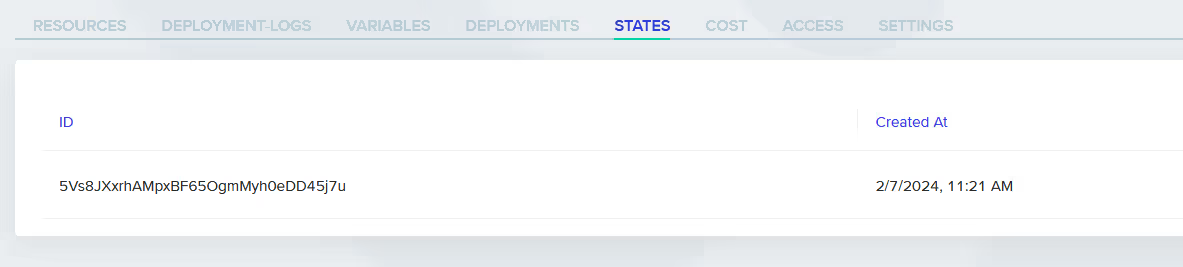
Our last step is to confirm the environment is set up and working properly.
Test an Environment
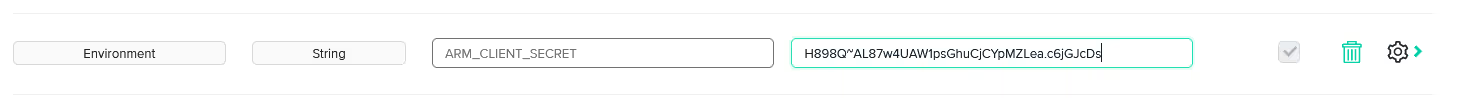
In the [.code]shared-network-dev[.code] environment, we’ll first update the [.code]ARM_CLIENT_SECRET[.code] environment variable with the correct value.
And then kick off a Redeploy action to verify that the environment matches the actual infrastructure deployed in Azure. After a few minutes, the plan comes back that no changes are required, meaning that the infrastructure matches the configuration.
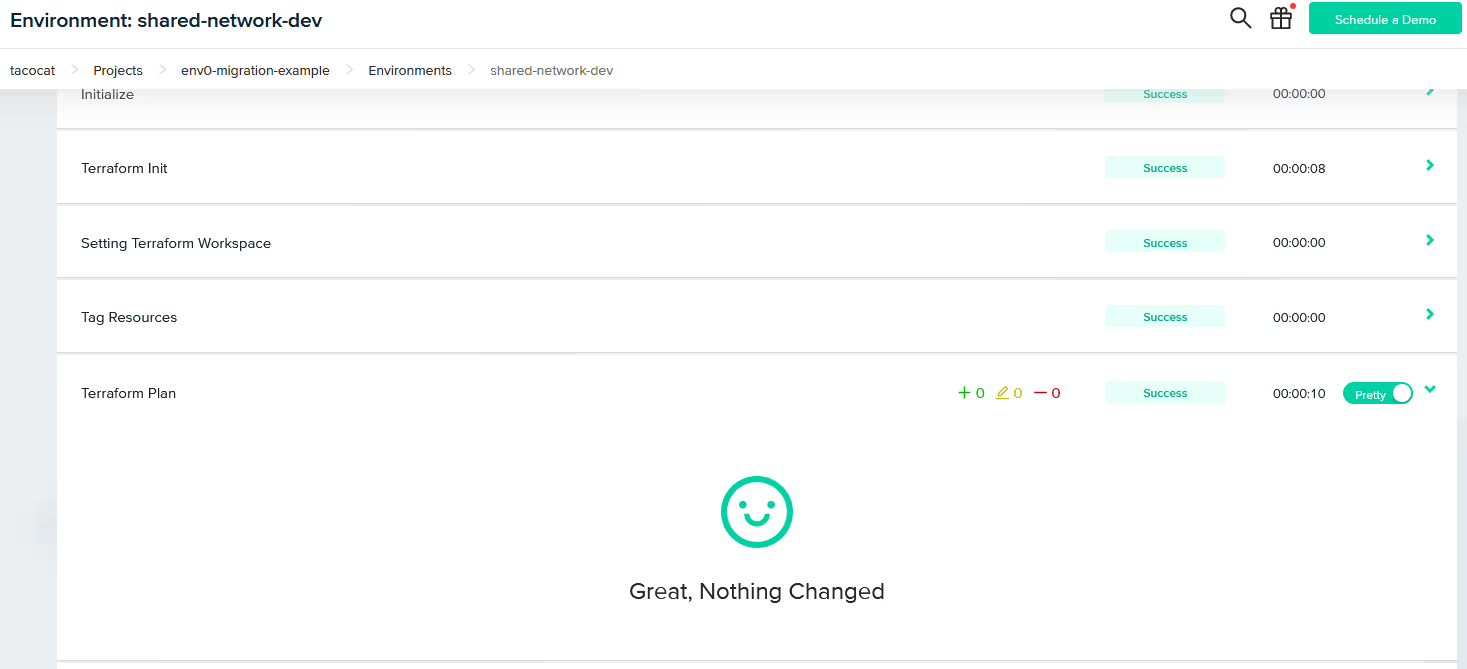
Success!
We have migrated our workspaces from Terraform Cloud to env zero without impacting the actual infrastructure!
Key Points to Note for a Successful Migration
Here are a few considerations and aspects to keep in mind for a smooth experience:
- You will need to be able to run a bash script for state migration.
- Workspaces that have a VCS workflow enabled are supported.
- Variable sets associated with a workspace or project are not exported.
- Permissions assigned to projects and workspaces are not exported.
- Modules stored in the private registry are not exported.
- Policy sets associated with the workspaces are not exported.
Post-migration setup and features
After completing the migration process, there are just a few tasks we recommend doing:
- Verify that your env zero account has access to the VCS repositories used by each workspace
- Configure permissions on each workspace to match Terraform Cloud
- Set up cloud provider credentials for each workspace if they were not part of the migrated variables
While you're at it, you can also take advantage of some excellent features of env zero:
- Drift Detection - Enables you to stay one step ahead of all discrepancies between target environments and source infrastructure code, enabling you also to create scheduled checks for infrastructure drift and notify your teams when an environment is in a drifted state.
- Cost Monitoring - Continuously tracks your actual cost, using patented technology, augmented by the ability to granularly set budget thresholds and auto-notifications.
- OPA Integration - Flexible way to configure Policy-as-Code for your environments using the Open Policy Agent. If you're already using OPA on Terraform Cloud, you can use the same policies with env zero.
What else you should know about env zero
Since you're already considering a migration to env zero, here are a few important things you should know about the platform:
It supports ALL the relevant frameworks
env zero goes beyond Terraform and OpenTofu, integrating effortlessly with additional tools like CloudFormation, Pulumi, Kubernetes, and Helm.
This is useful, especially for cloud-native environments that make heavy use of Helm and Kubernetes, being able to use a single platform to manage all of your Infrastructure as Code real estate is a huge time saver and lowers administrative overhead.
It's designed to offer maximal flexibility and enhanced reliability
env zero uses a hierarchy consisting of five layers, each of which can inherit settings and permissions from the parent scope. The five layers start at the organization, and then down through templates, projects, environments, and workflows.
Each layer can contain variable values to use in the workflow that is executed for an environment. Importantly, policies and permissions can also be applied at each scope, creating a robust management structure scaling well beyond a handful of environments.
This is especially helpful for organizations looking to expand IaC usage across different teams and promote managed self-service.
It streamlines complex environment management
Complex infrastructure architectures should be decoupled into separate configurations to simplify deployment and reduce the blast radius of changes. However, expressing dependencies across those configurations and sequencing the workflow can act as a barrier to adopting this practice.
env zero includes a multi-environment, tiered workflow option that allows you to express dependencies and deployment order of sub-environments using a declarative YAML file. And because env zero supports multiple frameworks, you can combine those frameworks in a single workflow to fully express your complex architecture.
It accelerates development processes with rapid iteration
env zero’s remote backend supports running remote operations from the command line to test uncommitted changes while still taking advantage of the custom workflows defined for an environment.
Developers can rapidly iterate through IaC testing and validation using their local environment before formally promoting changes through VCS, improving developer productivity and streamlining the change process.
Even better, you are not required to store state data on env zero’s remote backend to take advantage of remote operations.
Some customers must store state data in their own self-hosted backend, and we’re happy to provide the best of both worlds, flexible state data hosting and remote operations.
Wrap up
Infrastructure engineers should be able to pick the solution that meets their needs today and be able to shift to a different solution if the need arises. env zero’s Terraform Cloud migration tool helps do just that, simplifying and automating the process of migrating your Terraform Cloud workspaces to the platform.
To learn more about this and other env zero features, schedule a demo with a technical expert to see the platform in action.

.webp)




