
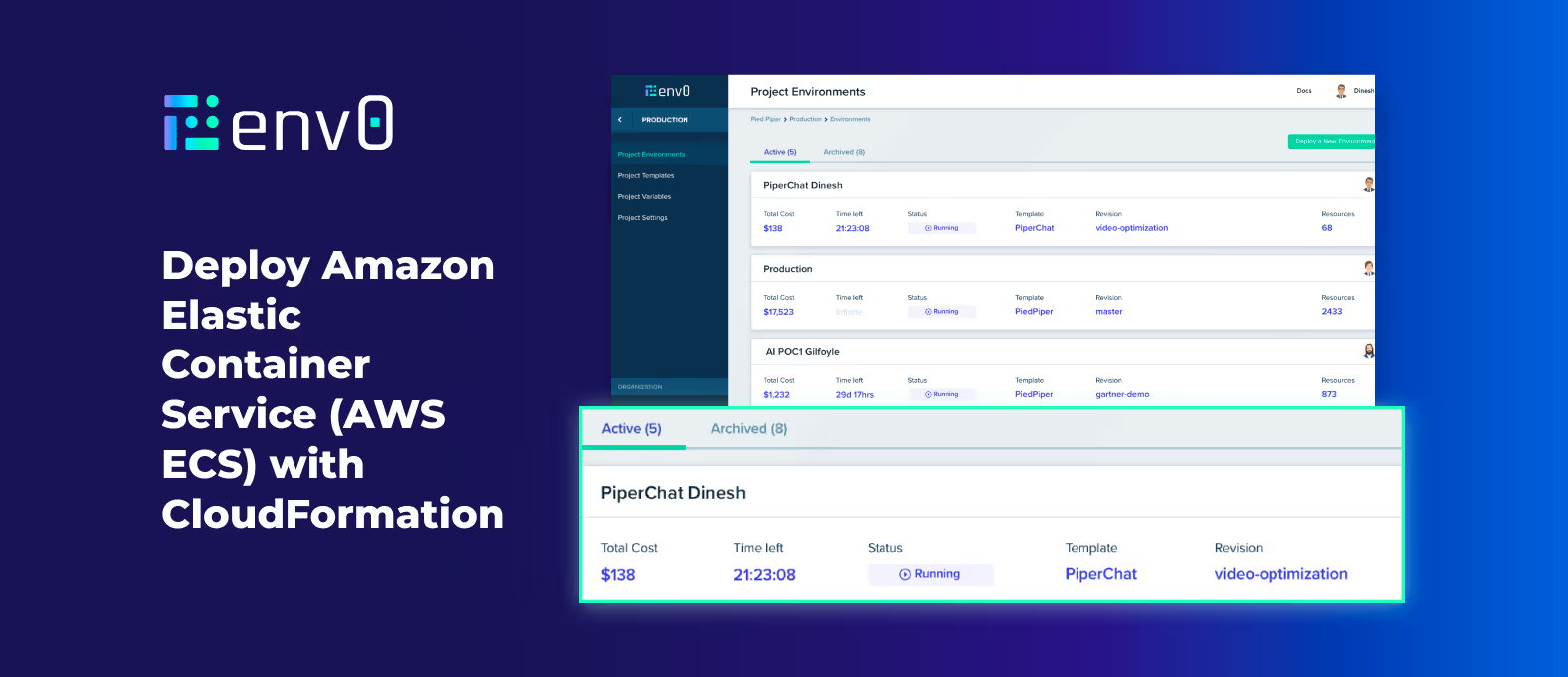
For any infrastructure or cloud service deployment, organizations need a way to make the entire deployment process repeatable. Not just for automation purposes, but to create a true standard that teams can use to be more efficient and keep multiple services running as expected.
In this blog post, you’ll learn how to combine AWS CloudFormation and env0 to create a production-driven experience for AWS Elastic Container Service Amazon ECS.
Why CloudFormation and Infrastructure as Code instead of ClickOps?
Let’s say you want to deploy a new service in AWS using ECS. What are the steps?
First, you’d have to log into the AWS console, then, you’d need to search for the right AWS service. Next, you’d go through three to four pages of the UI clicking drop downs and entering information to define your configuration. Finally, the ECS cluster will begin to deploy.
In short, without IaC, it’s a manual and cumbersome process. There’s no way to set a standard around it because even though it’s the same screen/UI that every engineer will see, there’s no way to determine that the same configuration is entered into the UI by each engineer. For example, one engineer might add one VPC and another might accidentally add a completely different VPC. There's no control to automate the process and make it repeatable for each team within the UI.
That’s where IaC, and in this example, CloudFormation comes into play.
CloudFormation is an Infrastructure as Code (IaC) tool designed to allow engineers to create AWS services as code. Instead of clicking around a UI, developers can define the individual services they’re using in a CloudFormation template called a stack (configured in a JSON or YAML file), upload the configuration to source control (like GitHub), and share it across teams. Using the AWS Command Line Interface (AWS CLI) to create AWS resources using Cloudformation stacks enables better collaboration, scale, and more secure deployments because developers in an organization can work together to create standardized practices. Platform Engineering (or DevOps, if you’d prefer) teams are then able to turn their existing AWS environments into scalable, repeatable offerings to the business units they support.
What’s ECS?
Amazon Elastic Container Service (AWS ECS) is a fully managed container orchestration service. It allows you to run and manage Docker containers on a cluster of Amazon Elastic Compute Cloud (Amazon EC2) instances. With ECS, you can deploy and manage your containerized applications easily, without the need to manage the underlying infrastructure.
Amazon ECS runs as a service in AWS cloud and is AWS specific. It allows you to deploy a container from a container image and run it with full scalability and scheduling capabilities. You can either run Amazon ECS with an AWS Fargate profile (no EC2 instance backend) or with Amazon EC2 instances running as the Amazon ECS backend.
Although Kubernetes is a great orchestration platform—and to be honest, it’s the most popular right now which means more support options and more tooling options—it’s not the only orchestration platform out there to manage your containerized workloads.
Amazon ECS is what some engineers like to call “Kubernetes lite.” It has all of the orchestration, scheduling, and scalability features that Kubernetes has for containers. It just doesn’t have as many customizable features, which is sometimes good for organizations. Especially if they have limited resources, or a relatively small set of requirements for their containerized applications.
Now that you have some theory behind AWS CloudFormation and Amazon ECS, let’s jump into the hands-on piece of this blog post.
Prerequisites
To follow along, you will need the following:
- An env0 account (free trial signup)
- A source control repo such as GitHub to store the code in for deployment purposes (demo repo)
- An AWS account (you can sign up for a free trial/tier here)
Before deploying the AWS CloudFormation code to create an ECS cluster, you’ll first need to authenticate to AWS via env0.
First, ensure that you either have:
These are the two options available to authenticate env0 to deploy AWS Services.
For the purposes of this blog post, you’ll learn how to utilize the “AWS access/secret keys” method.
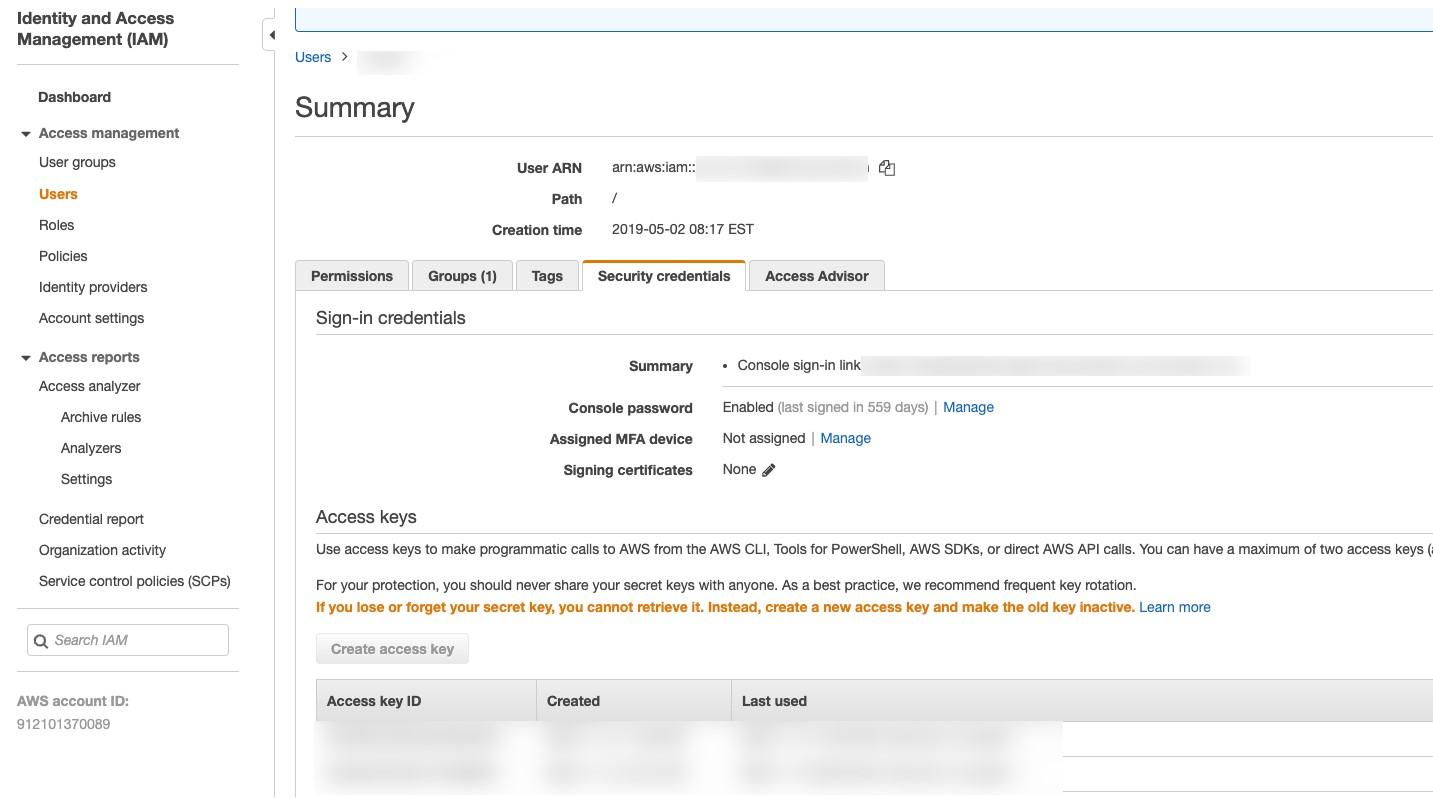
Log into the AWS portal, choose a user that has appropriate access, and generate an access/secret key underneath Security credentials.
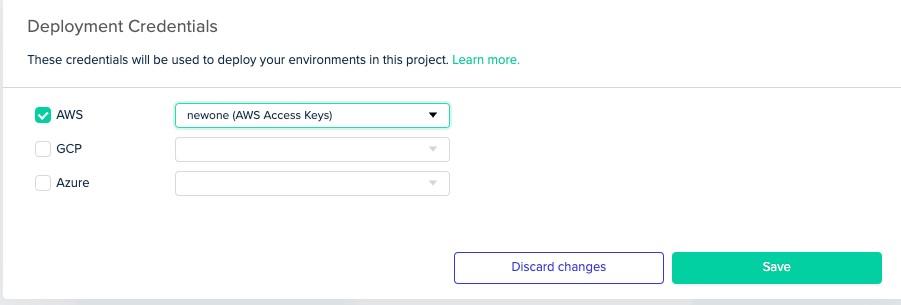
Next, log into env0 and under Project Settings, click on CREDENTIALS and choose the AWS option.

Click the green + Add Credential button.
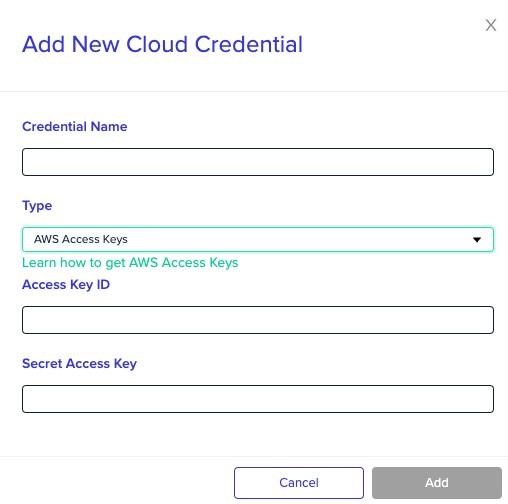
Under the Add New Cloud Credential page, give your credential a name (this is anything you want it to be). Then, add in your access key and secret key.
You’ll now see your credential as an option.
Click the green Save button.
The AWS CloudFormation code
Now that the AWS credential is added, you can start thinking about the code that you want to deploy with env0.
Before showcasing the CloudFormation all together, let’s break down our example.
First, you have the resource that you’re creating.
AWSTemplateFormatVersion: “2010-09-09”
Resources:
Cluster:
Type: AWS::ECS::Cluster
Next, you have the resource properties for the cluster name.
Properties:
ClusterName: ecsclusternv0
After you define the key properties, you can set up the log group.
LogGroup:
Type: AWS::Logs::LogGroup
Properties:
LogGroupName: ecs-log-group
The last step is to configure the IAM role and policies needed to run ECS.
ExecutionRole:
Type: AWS::IAM::Role
Properties:
RoleName: ecs-deployment-role
AssumeRolePolicyDocument:
Statement:
- Effect: Allow
Principal:
Service: ecs-tasks.amazonaws.com
Action: sts:AssumeRole
ManagedPolicyArns:
- arn:aws:iam:aws:policy/service-role/AmazonECSTaskExecutionRolePolicy
All together, the code looks like the below.
AWSTemplateFormatVersion: “2010-09-09”
Resources:
Cluster:
Type: AWS::ECS::Cluster
Properties:
ClusterName: ecsclusternv0
LogGroup:
Type: AWS::Logs::LogGroup
Properties:
LogGroupName: ecs-log-group
ExecutionRole:
Type: AWS::IAM::Role
Properties:
RoleName: ecs-deployment-role
AssumeRolePolicyDocument:
Statement:
- Effect: Allow
Principal:
Service: ecs-tasks.amazonaws.com
Action: sts:AssumeRole
ManagedPolicyArns:
- arn:aws:iam:aws:policy/service-role/AmazonECSTaskExecutionRolePolicy
Ensure you save the code to your Git repo that’ll be used for the deployment with env0.
Deploy AWS ECS Resources with CloudFormation and env0
Now that the code is defined, you can deploy it via env0.
First, create a new environment.
Next, choose the VCS option to specify a source control path. (This convenient option allows you to spin up a new resource on demand simply by referring to infrastructure code you've already written, instead of creating a new template.)
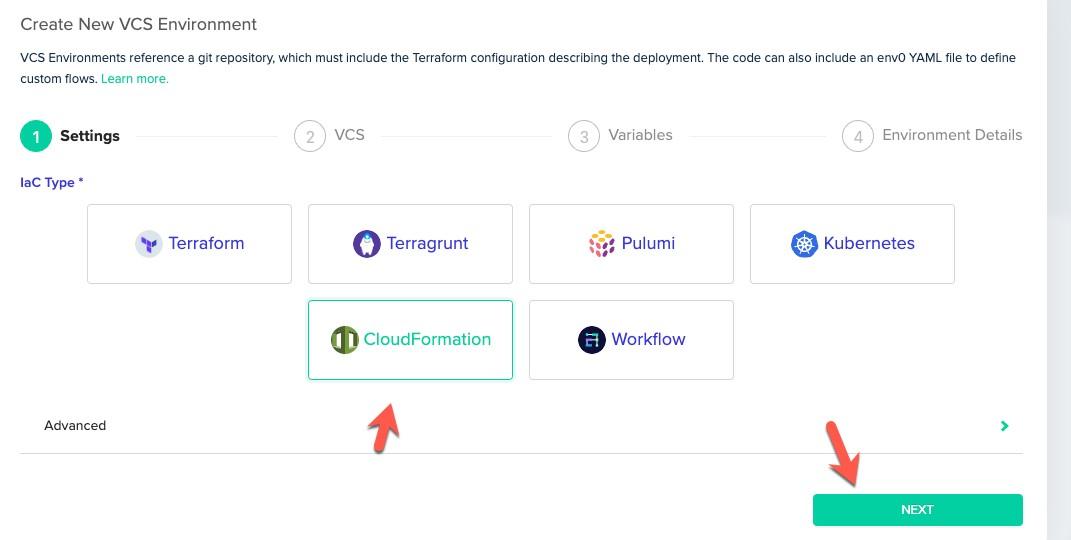
Ensure that you choose CloudFormation as the VCS environment.
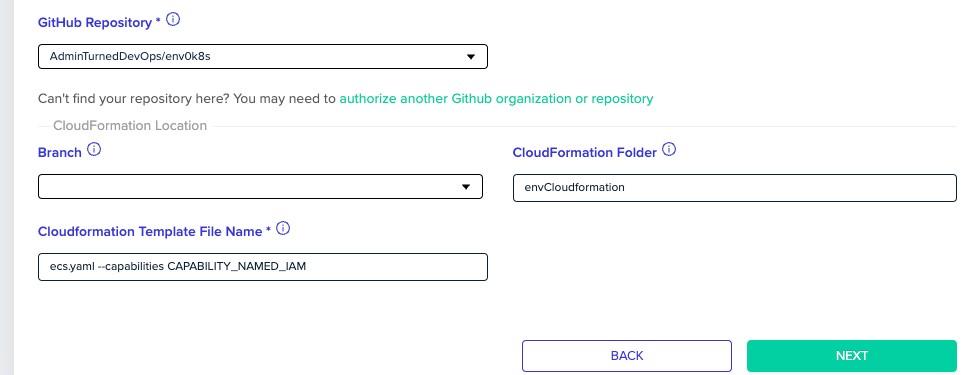
Add in your Git repo and where the CloudFormation template exists.
When specifying the CloudFormation template file, ensure that you add the `capabilities` flag. The reason is that you have to explicitly tell CloudFormation that you are OK with create the new permissions.
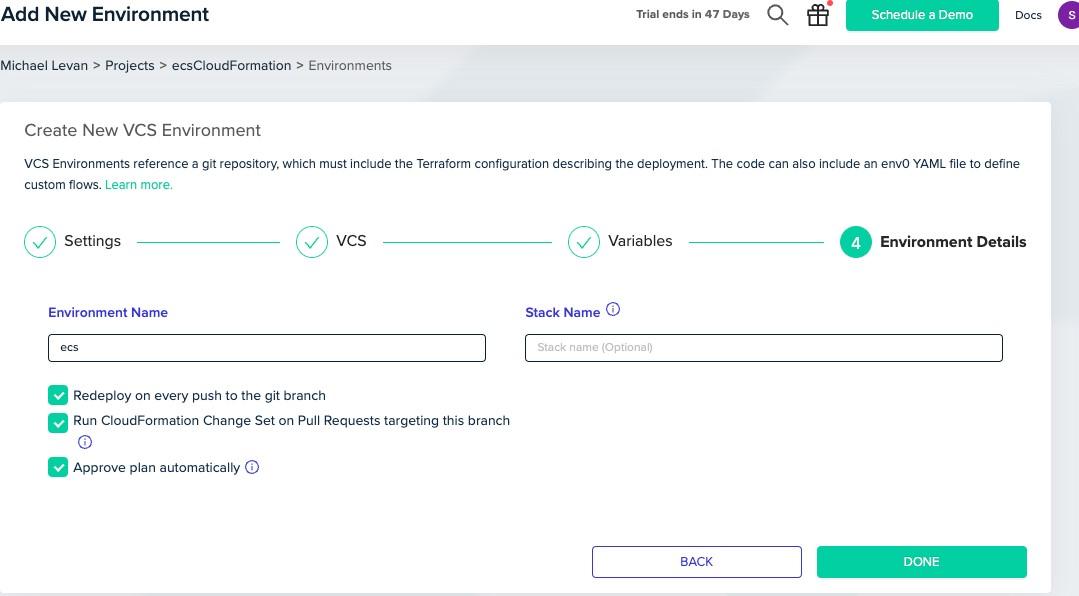
Give your new AWS environment a name.
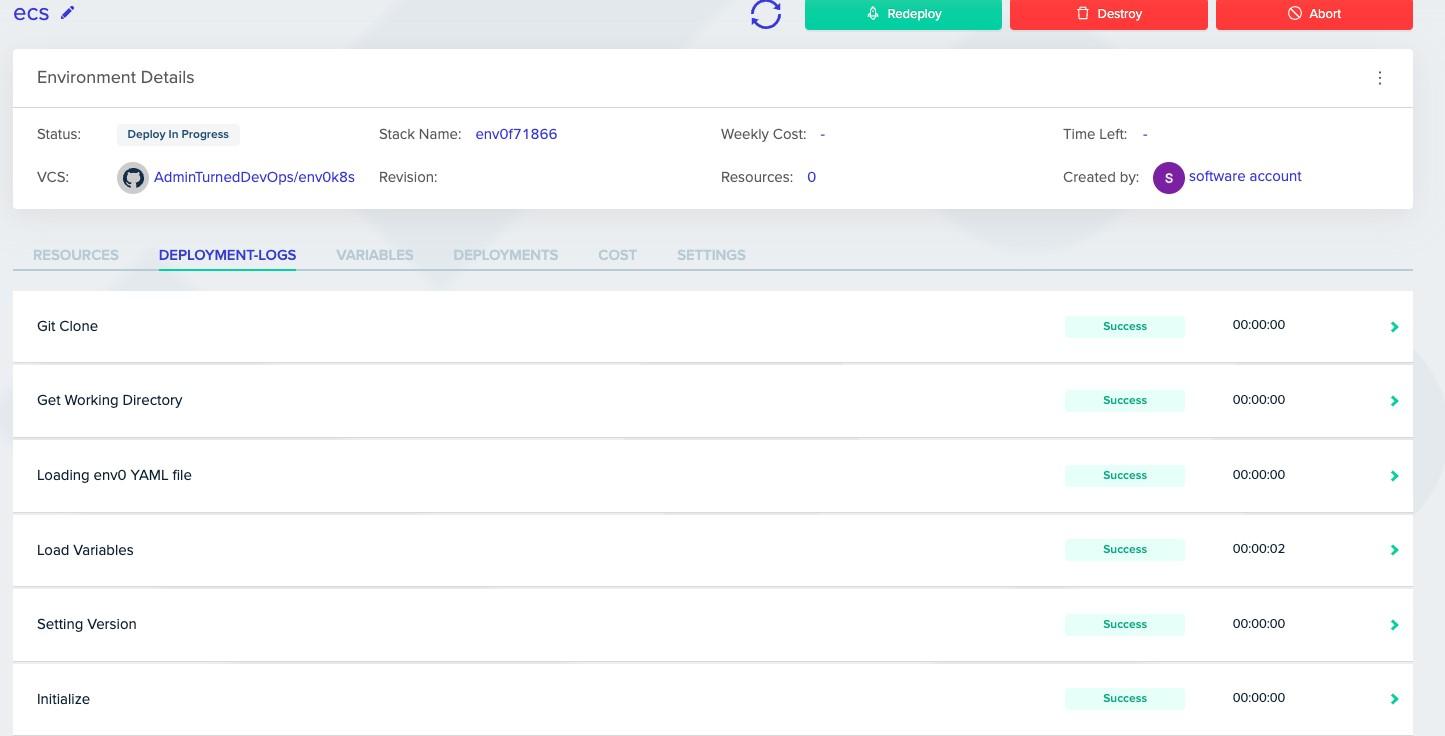
As in the screenshot below, you should see that the CloudFormation stack has started.
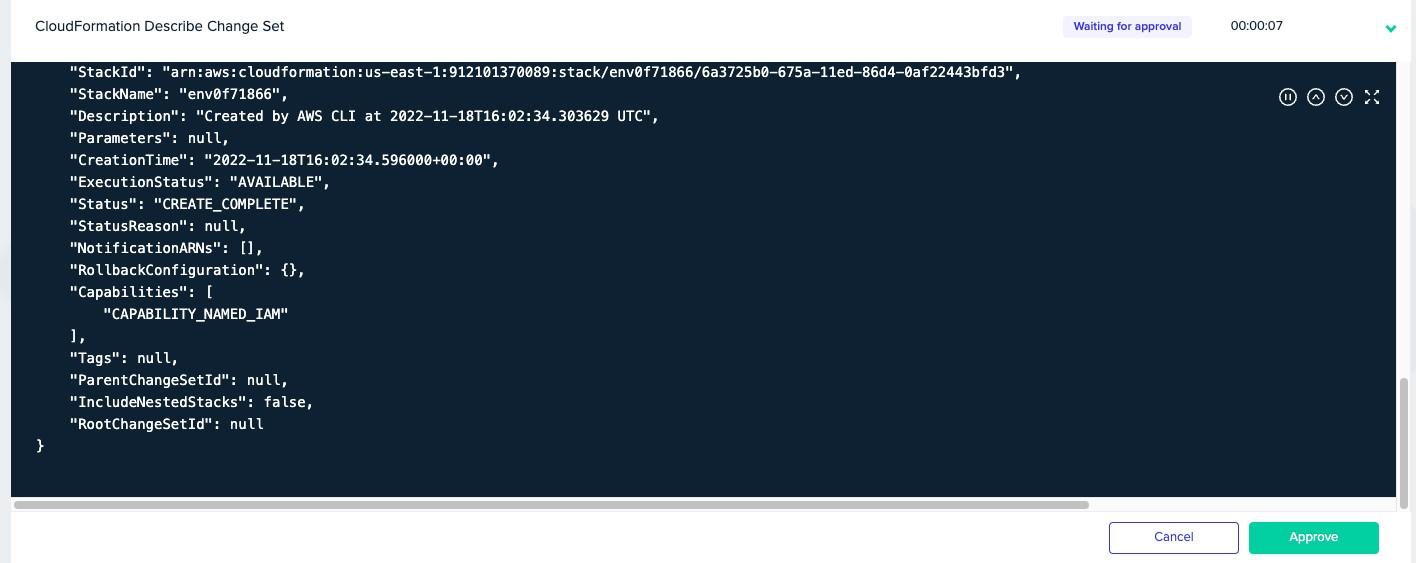
If you have an approval workflow, inspect the details in the CloudFormation Describe Change Set output, then approve the stack creation.
Once complete, you should see that the stack has been successfully deployed and the Amazon ECS cluster is now created.

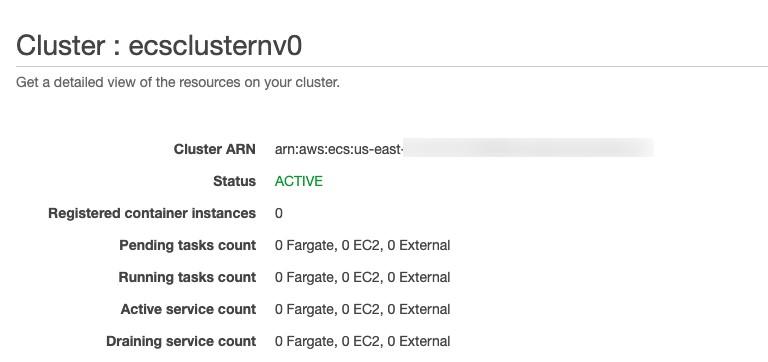
Deploy AWS ECS With CloudFormation and env0. Back in the AWS console, we can see the instances have been deployed. now we’re ready to deploy infrastructure and applications into our ECS cluster.
For more information check out this blog where we compareTerraform vs Cloudformation and show how they can be used with env0 platform.

.webp)




